You are here
Technology
PHP sinks in Tiobe language popularity index
PHP, long a popular server-side scripting language for web development, has dropped to its lowest position ever in the monthly Tiobe index of programming language popularity, ranking 17th in the April 2024 edition of the index.
When the Tiobe index started in 2001, PHP was about to become the standard language for building websites, said Paul Jansen, CEO of software quality services vendor Tiobe. PHP even reached the top 3 spot in the index, ranking third several times between 2006 and 2010. But as competing web development frameworks such as Ruby on Rails, Django, and React arrived in other languages, PHP’s popularity waned.
Progress in AI requires thinking beyond LLMs
We need to have a frank conversation about large language models (LLMs). At their core, LLMs are nothing more than sophisticated memorization machines, capable of reasonable-sounding statements, but unable to understand fundamental truth. Importantly and despite the fervent hopes of many, they are far from delivering or even prefiguring artificial general intelligence (AGI). The hype surrounding LLMs has reached stratospheric levels, fostering a misguided belief in their potential as AGI precursors.
We find ourselves at a critical juncture where the erroneous linkage between LLMs and AGI threatens to slow down—not accelerate—genuine progress in artificial intelligence. The clamor for LLMs to evolve into AGI solutions epitomizes tunnel vision at its finest. Consider the vast investments poured into training ever-larger models, yielding only marginal improvements in tasks that are not text-based. Let’s face it: LLMs are not learning how to do mathematics. Their forte lies in tackling statistical text tasks with finesse. It’s imperative that we recalibrate expectations and acknowledge that although LLMs excel in certain domains, they fall short in others.
How to talk to machines: 10 secrets of prompt engineering
Just a few years ago, a prompt was something English teachers used for homework assignments, which filled up weekends and kept students inside on sunny days. Now it seems we’re all teachers, tasked with distributing perfect prompts that direct large language models to do our bidding. These prompts are also endowed with the power to ruin weekends, but it’s not the machines that are suffering.
The power of prompts can seem downright magical. We toss off a few words that approximate a human language and, voila! Back comes a nicely formatted, well-structured answer to whatever question we asked. No topic is too obscure and no fact is out of our reach. At least as long as it’s part of the training corpus and approved by the model’s shadowy controllers.
How to test large language models
There’s significant buzz and excitement around using AI copilots to reduce manual work, improving software developer productivity with code generators, and innovating with generative AI. The business opportunities are driving many development teams to build knowledge bases with vector databases and embed large language models (LLMs) into their applications.
Rapid B2B integrations with Ballerina and Choreo
Many business processes involve communicating with external parties such as suppliers, logistics providers, insurance providers, and government institutions. Unlike internal communications, these inter-organizational communications usually have to follow various regulations and standards, and could introduce delays if one party doesn’t comply. Therefore, effective business-to-business (B2B) integrations are a key part of most digital transformation projects.
Let’s take the fictional example of an electronic equipment manufacturer named Smartware. Smartware supplies equipment for multiple retailers and depends on multiple suppliers and logistics partners for fulfilling orders. Their order processing workflow can be depicted as follows:
TWiT 974: Get at the Young Youngs - Tesla Robotaxi, Marissa Mayer's Sunshine
- House, Senate leaders nearing deal on landmark online privacy bill
- Marissa Mayer's eternal Sunshine
- Elon Musk says Tesla will unveil its robotaxi on Aug. 8; shares pop
- Amazon's Grocery Stores to Drop Just Walk Out Checkout Tech
- X's 'complimentary' Premium push gives people blue checks they didn't ask for
- President Biden is now posting into the fediverse
- Yahoo is acquiring Artifact to bring its AI features to Yahoo News
- MrBeast calls for slowing down video editing styles
- A TikTok Whistleblower Got DC's Attention. Do His Claims Add Up?
- Price of zero-day exploits rises as companies harden products against hackers
- App Store guidelines now allow game emulators; more
- How Tech Giants Cut Corners to Harvest Data for A.I.
- Google Pledges to Destroy Browsing Data to Settle 'Incognito' Lawsuit
- SF Giants using facial recognition tech to fast-track ticket line
- Apple (AAPL) Explores Home Robots After Abandoning Car Efforts
Host: Leo Laporte
Guests: Mikah Sargent, Lisa Schmeiser, and Harry McCracken
Download or subscribe to this show at https://twit.tv/shows/this-week-in-tech
Get episodes ad-free with Club TWiT at https://twit.tv/clubtwit
Sponsors:
Eclipse joins with industry groups to secure open source
The Eclipse Foundation announced that it is partnering with the Apache Software Foundation and other open source foundations to establish common specifications for secure software development based on existing open source best practices.
In an April 2 blog post, Eclipse said that the goal of the initiative was to meet the challenges of cybersecurity in the open source ecosystem and demonstrate cooperation with the European Union’s Cyber Resilience Act (CRA). Participants include Apache, Eclipse, the Rust Foundation, the PHP Foundation, the Blender Foundation, the OpenSSL Software Foundation, and the Python Software Foundation.
Microsoft’s Azure AI Search updated with increased storage, vector index size
Microsoft has updated its Azure AI Search service to increase storage capacity and vector index size at no additional cost, a move it said will make it more economical for enterprises to run generative AI-based applications.
Formerly known as Azure Cognitive Search, the Azure AI Search service connects external data stores containing un-indexed data with an application that sends queries or requests to a search index. It consists of three components—a query engine, indexes, and the indexing engine—and is mostly used in retrieving information to enhance the performance of generative AI, a process known as retrieval-augmented generation (RAG).
Cohere launches new Command R+ LLM on Azure first
Cohere has unveiled its latest large language model (LLM), Command R+, which is engineered to enhance enterprise workflows and applications.
The company said the new model is its most advanced and scalable LLM yet. Building on the foundations of the earlier Command R model, Command R+ boosts performance for various enterprise tasks, including data categorization and workflow automation, the company said.
Although Cohere said in March that it would train and deploy its models on Oracle Cloud Infrastructure (OCI) under its partnership with Oracle, it has chosen to make Command R+ available first on Microsoft Azure. The software is set to launch on OCI shortly, with plans to expand to more cloud platforms in the upcoming weeks, said Cohere spokesman Kyle Lastovica. It’s already available through Cohere’s own hosted API.
AI advancements are fueling cloud infrastructure spending
The latest data from the IDC Worldwide Quarterly Enterprise Infrastructure Tracker paints a compelling picture of growth in cloud infrastructure sales on demand. The fourth quarter of 2023 saw an 18.5% year-over-year increase in spending on compute and storage infrastructure for cloud deployments. It is a significant shift in the technological landscape, where AI is now front and center in the push to find cloud infrastructure to run it.
The spending surge indicates shifting budgets; a contrasting trend is the decline in the total number of units shipped. IDC says this shows a strategic move towards high-capacity, GPU-heavy servers with higher average price tags favored by hyperscalers. The idea is that these servers can do more than those driven by traditional CPU-based servers, thus, you need fewer.
Speed up searches using SearchValues in .NET
With the release of .NET 8, Microsoft introduced a plethora of new features and enhancements in the .NET Core and ASP.NET Core frameworks. One such feature is the SearchValues class, which marks a significant step forward in efficiently fetching data from data sets.
SearchValues is a new type introduced in .NET 8 designed to improve application performance. By using optimization techniques like vectorization and hardware acceleration, SearchValues delivers speed enhancements while seamlessly blending with .NET Core and ASP.NET Core.
In this article, we’ll explain how you can use SearchValues to improve the speed of searches in .NET Core applications.
Visual Studio Code finalizes test coverage API
Microsoft has unveiled Visual Studio Code 1.88, also known as the March 2024 release of the company’s popular code editor. The update brings capabilities such as a test coverage API, custom editor labels, and locked scrolling.
Introduced on April 4, Visual Studio Code 1.88 can be downloaded for Windows, Linux, or Mac from the project website.
In this release, Microsoft has finalized its Test Coverage API, bringing native coverage support to VS Code. If a developer’s testing system supports it, coverage can be accessed using the new Run With Coverage button. Using test coverage requires that your VS Code extension implements the new API.
JetBrains IDEs add AI-powered code autocompletion
JetBrains has added full-line code autocompletion to its family of IDEs (integrated development environments), powered by locally run AI models. Full line code complеtion is available for Java, Kotlin, Python, JavaScript, TypeScript, CSS, PHP, Go, and Ruby with the 2024.1 versions of the respective IDEs.
Fake Lawsuit Threat Exposes Privnote Phishing Sites
A cybercrook who has been setting up websites that mimic the self-destructing message service privnote.com accidentally exposed the breadth of their operations recently when they threatened to sue a software company. The disclosure revealed a profitable network of phishing sites that behave and look like the real Privnote, except that any messages containing cryptocurrency addresses will be automatically altered to include a different payment address controlled by the scammers.
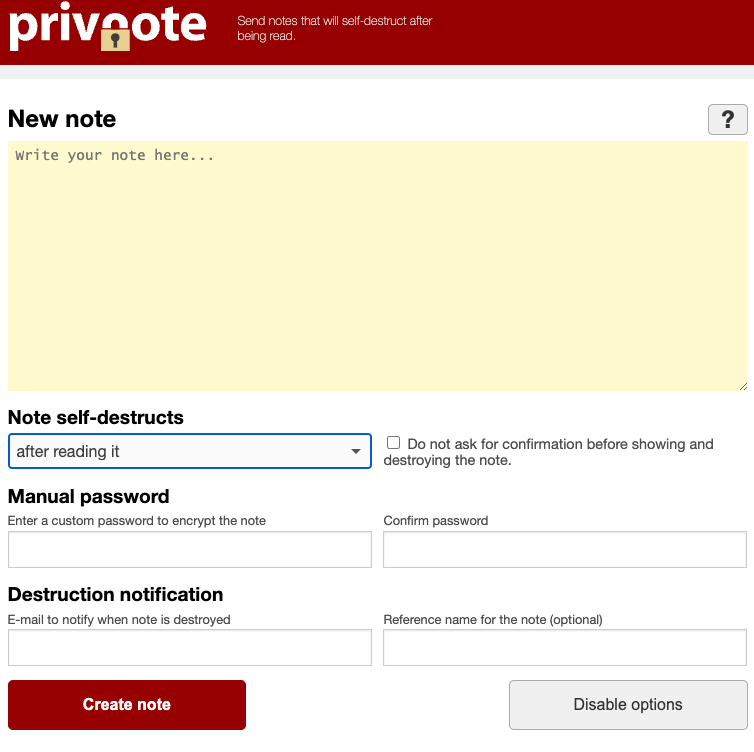
The real Privnote, at privnote.com.
Launched in 2008, privnote.com employs technology that encrypts each message so that even Privnote itself cannot read its contents. And it doesn’t send or receive messages. Creating a message merely generates a link. When that link is clicked or visited, the service warns that the message will be gone forever after it is read.
Privnote’s ease-of-use and popularity among cryptocurrency enthusiasts has made it a perennial target of phishers, who erect Privnote clones that function more or less as advertised but also quietly inject their own cryptocurrency payment addresses when a note is created that contains crypto wallets.
Last month, a new user on GitHub named fory66399 lodged a complaint on the “issues” page for MetaMask, a software cryptocurrency wallet used to interact with the Ethereum blockchain. Fory66399 insisted that their website — privnote[.]co — was being wrongly flagged by MetaMask’s “eth-phishing-detect” list as malicious.
“We filed a lawsuit with a lawyer for dishonestly adding a site to the block list, damaging reputation, as well as ignoring the moderation department and ignoring answers!” fory66399 threatened. “Provide evidence or I will demand compensation!”
MetaMask’s lead product manager Taylor Monahan replied by posting several screenshots of privnote[.]co showing the site did indeed swap out any cryptocurrency addresses.
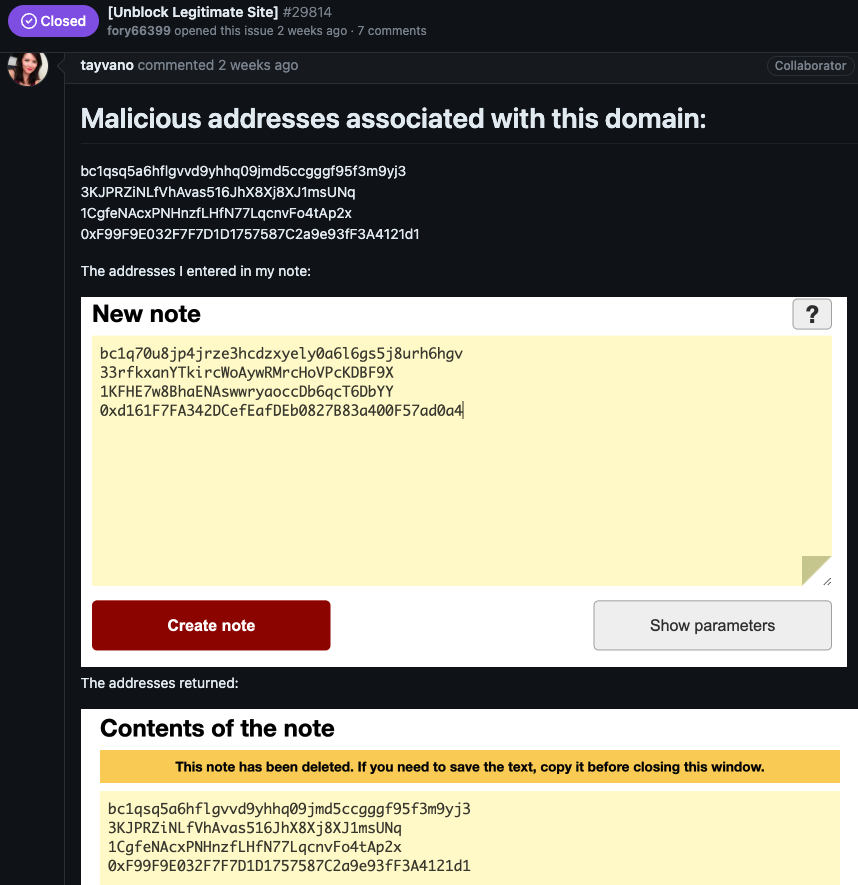
After being told where they could send a copy of their lawsuit, Fory66399 appeared to become flustered, and proceeded to mention a number of other interesting domain names:
You sent me screenshots from some other site! It’s red!!!!
The tornote.io website has a different color altogether
The privatenote,io website also has a different color! What’s wrong?????
A search at DomainTools.com for privatenote[.]io shows it has been registered to two names over as many years, including Andrey Sokol from Moscow and Alexandr Ermakov from Kiev. There is no indication these are the real names of the phishers, but the names are useful in pointing to other sites targeting Privnote since 2020.
DomainTools says other domains registered to Alexandr Ermakov include pirvnota[.]com, privatemessage[.]net, privatenote[.]io, and tornote[.]io.
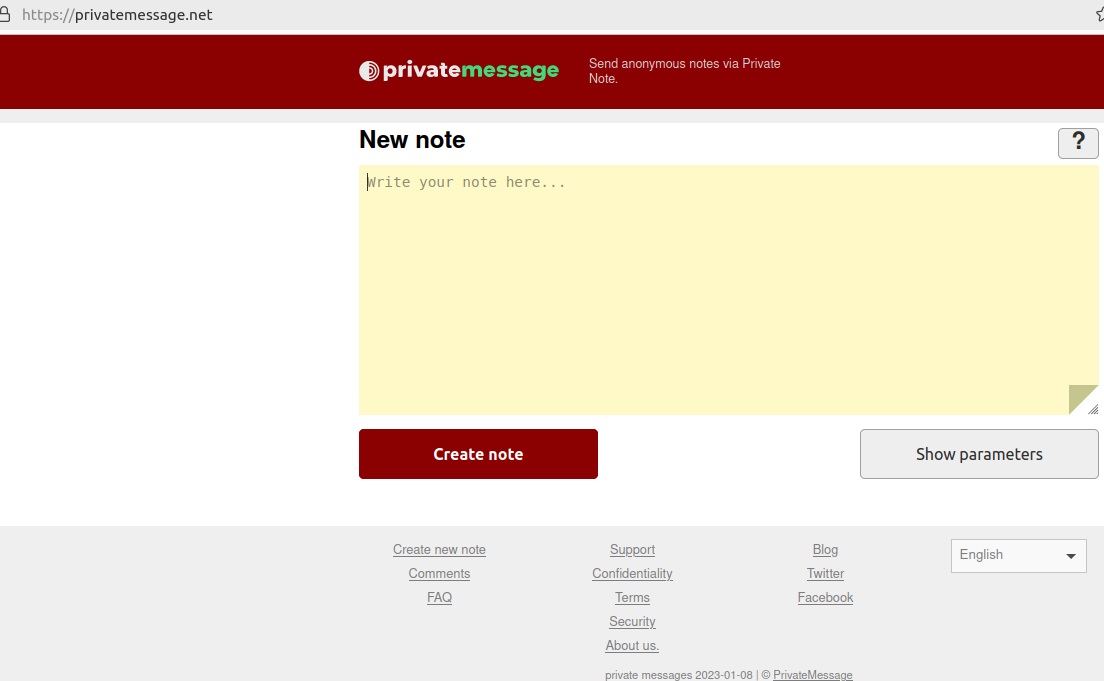
A screenshot of the phishing domain privatemessage dot net.
The registration records for pirvnota[.]com at one point were updated from Andrey Sokol to “BPW” as the registrant organization, and “Tambov district” in the registrant state/province field. Searching DomainTools for domains that include both of these terms reveals pirwnote[.]com.
Other Privnote phishing domains that also phoned home to the same Internet address as pirwnote[.]com include privnode[.]com, privnate[.]com, and prevnóte[.]com. Pirwnote[.]com is currently selling security cameras made by the Chinese manufacturer Hikvision, via an Internet address based in Hong Kong.
It appears someone has gone to great lengths to make tornote[.]io seem like a legitimate website. For example, this account at Medium has authored more than a dozen blog posts in the past year singing the praises of Tornote as a secure, self-destructing messaging service. However, testing shows tornote[.]io will also replace any cryptocurrency addresses in messages with their own payment address.
These malicious note sites attract visitors by gaming search engine results to make the phishing domains appear prominently in search results for “privnote.” A search in Google for “privnote” currently returns tornote[.]io as the fifth result. Like other phishing sites tied to this network, Tornote will use the same cryptocurrency addresses for roughly 5 days, and then rotate in new payment addresses.
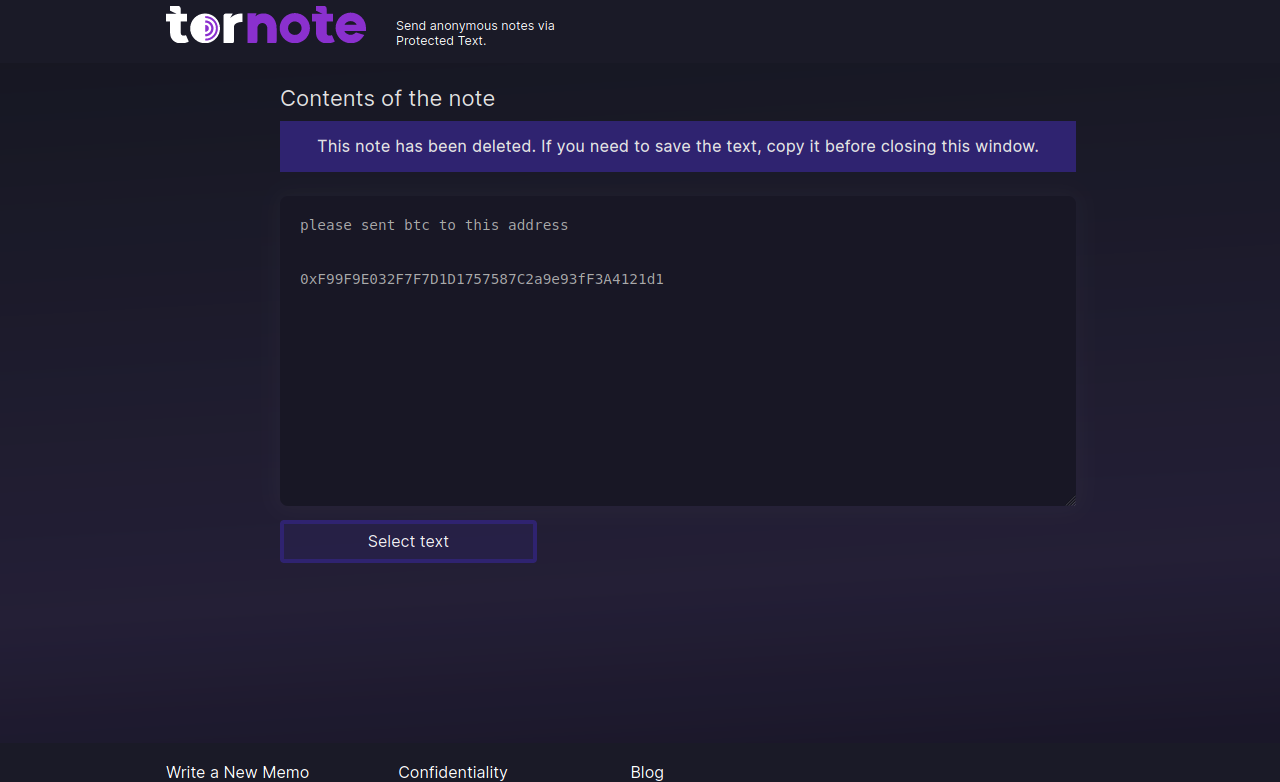
Tornote changed the cryptocurrency address entered into a test note to this address controlled by the phishers.
Throughout 2023, Tornote was hosted with the Russian provider DDoS-Guard, at the Internet address 186.2.163[.]216. A review of the passive DNS records tied to this address shows that apart from subdomains dedicated to tornote[.]io, the main other domain at this address was hkleaks[.]ml.
In August 2019, a slew of websites and social media channels dubbed “HKLEAKS” began doxing the identities and personal information of pro-democracy activists in Hong Kong. According to a report (PDF) from Citizen Lab, hkleaks[.]ml was the second domain that appeared as the perpetrators began to expand the list of those doxed.
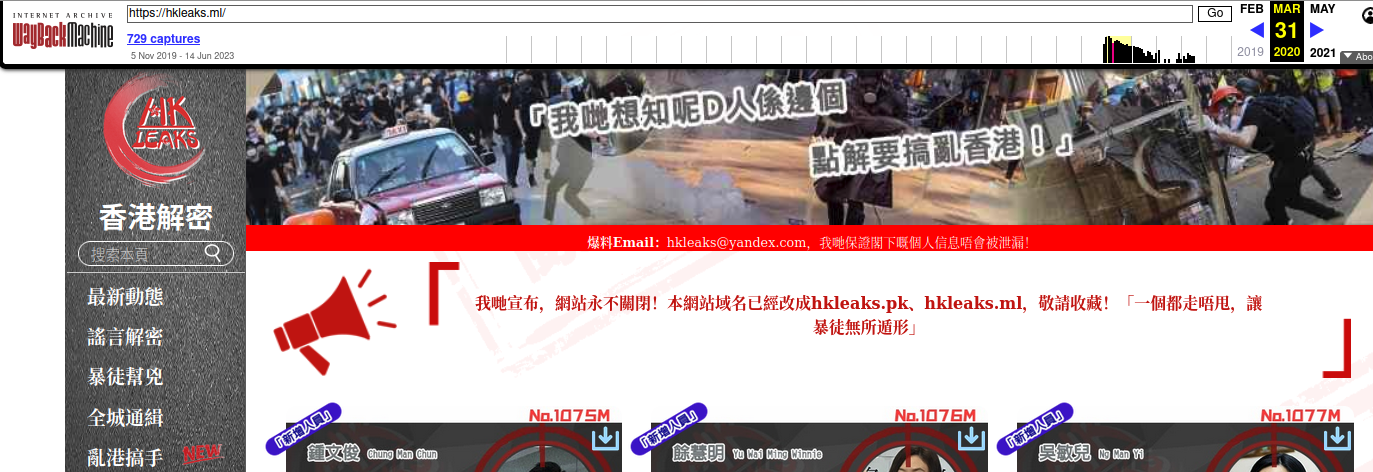
HKleaks, as indexed by The Wayback Machine.
The address 186.2.163[.]216 also is home to the website rustraitor[.]info, a website erected after Russia invaded Ukraine in early 2022 that doxed Russians perceived to have helped the Ukrainian cause.
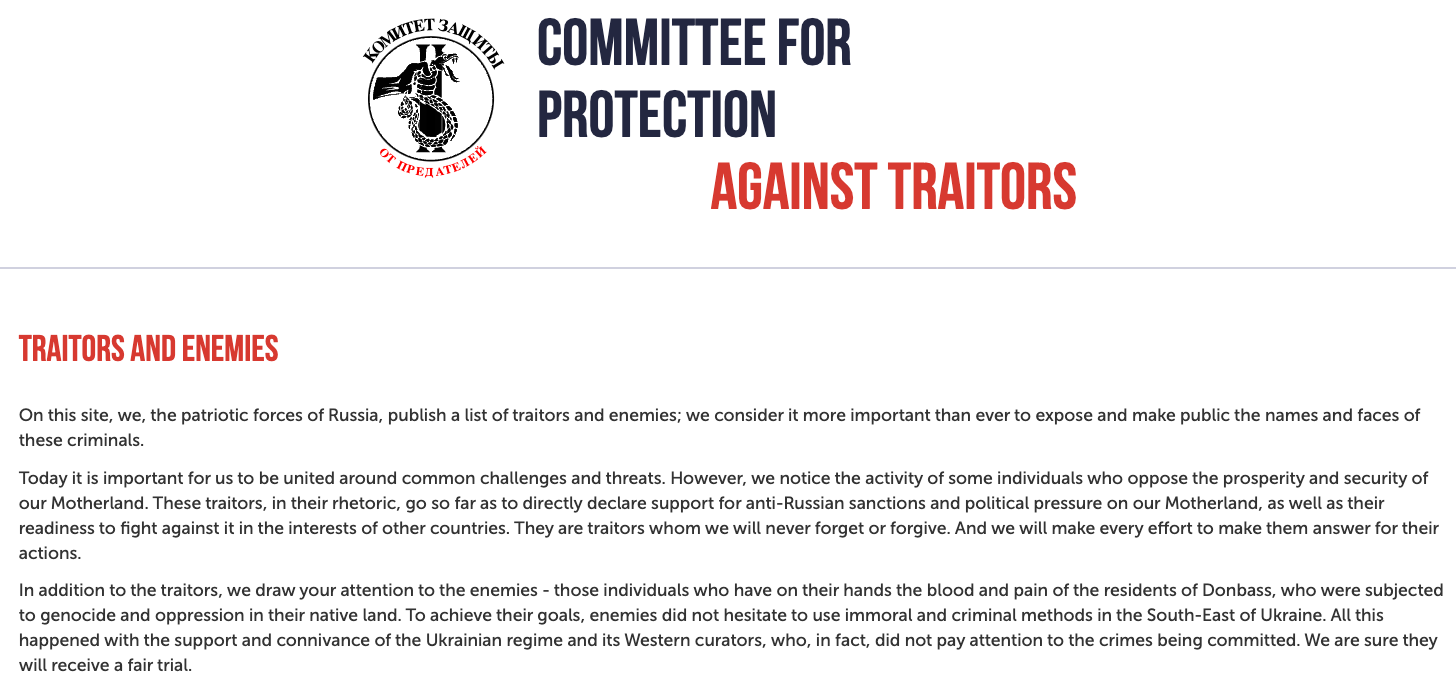
An archive.org copy of Rustraitor.
DomainTools shows there are more than 1,000 other domains whose registration records include the organization name “BPW” and “Tambov District” as the location. Virtually all of those domains were registered through one of two registrars — Hong Kong-based Nicenic and Singapore-based WebCC — and almost all appear to be phishing or pill-spam related.
In keeping with the overall theme, these phishing domains appear focused on stealing usernames and passwords to some of the cybercrime underground’s busiest shops, including Brian’s Club. What do all the phished sites have in common? They all accept payment via virtual currencies.
It appears MetaMask’s Monahan made the correct decision in forcing these phishers to tip their hand: Among the websites at that DDoS-Guard address are multiple MetaMask phishing domains, including metarrnask[.]com, meternask[.]com, and rnetamask[.]com.
How profitable are these private note phishing sites? Reviewing the four malicious cryptocurrency payment addresses that the attackers swapped into notes passed through privnote[.]co (as pictured in Monahan’s screenshot above) shows that between March 15 and March 19, 2024, those address raked in and transferred out nearly $18,000 in cryptocurrencies. And that’s just one of their phishing websites.
DataStax acquires Langflow creator Logspace to aid gen AI app development
Database and related services provider DataStax is acquiring Logspace, creator of the open source package Langflow, for an undisclosed sum, in order to help developers build generative AI applications faster, it said Thursday.
Langflow is an open-source, web-based no-code graphical user interface (GUI) that allows developers to visually prototype LangChain flows and iterate them to develop applications faster. LangChain is a modular framework for Python and JavaScript that simplifies the development of applications that are powered by generative AI language models or LLMs.
Using Neo4J’s graph database for AI in Azure
Once you get past the chatbot hype, it’s clear that generative AI is a useful tool, providing a way of navigating applications and services using natural language. By tying our large language models (LLMs) to specific data sources, we can avoid the risks that come with using nothing but training data.
While it is possible to fine-tune an LLM on specific data, that can be expensive and time-consuming, and it can also lock you into a specific time frame. If you want accurate, timely responses, you need to use retrieval-augmented generation (RAG) to work with your data.
RAG: the heart of Microsoft’s CopilotsThe neural networks that power LLMs are, at heart, sophisticated vector search engines that extrapolate the paths of semantic vectors in an n-dimensional space, where the higher the dimensionality, the more complex the model. So, if you’re going to use RAG, you need to have a vector representation of your data that can both build prompts and seed the vectors used to generate output from an LLM. That’s why it’s one of the techniques that powers Microsoft’s various Copilots.
How to build a developer-first company
At my company, Descope, we are building a customer authentication and identity management product, meaning the end user and the developer are two sides of the same coin. Providing a great developer experience—by enabling our customers to easily add auth flows and user management to their apps—leads to a great end-user experience as the customer’s customers seamlessly and securely log in.
This kind of virtuous cycle exists at many developer-focused companies. When building a successful developer-first business, it’s critical to tie together the similarities between the customer experience and the developer experience while clearly delineating the differences.
Easy MSP Wins in One Email
Discover why following up with past prospects could be an easy win for your MSP.
Source: Easy MSP Wins in One Email - Technibble.com
Google rolls out a new JPEG coding library
Google has introduced Jpegli, a JPEG library for image encoding. The new library is intended to be faster, more visually pleasing, and more efficient than traditional JPEGs. Proponents of the technology said it has the potential to make the Internet faster and more beautiful.
Announced April 3 and accessible from GitHub, Jpegli maintains high backward compatibility while offering enhanced capabilities and a 35% compression ratio at high-quality compression settings, Google said. Jpegli works by using new techniques to reduce noise and improve image quality. New or improved features include adaptive quantization heuristics from the JPEG XL reference implementation, improved quantization matrix selection, calculation of intermediate results, and the possibility to use more advanced colorspace.