You are here
Technology
Crooks Bypassed Google’s Email Verification to Create Workspace Accounts, Access 3rd-Party Services
Google says it recently fixed an authentication weakness that allowed crooks to circumvent the email verification required to create a Google Workspace account, and leverage that to impersonate a domain holder at third-party services that allow logins through Google’s “Sign in with Google” feature.

Last week, KrebsOnSecurity heard from a reader who said they received a notice that their email address had been used to create a potentially malicious Workspace account that Google had blocked.
“In the last few weeks, we identified a small-scale abuse campaign whereby bad actors circumvented the email verification step in our account creation flow for Email Verified (EV) Google Workspace accounts using a specially constructed request,” the notice from Google read. “These EV users could then be used to gain access to third-party applications using ‘Sign In with Google’.”
In response to questions, Google said it fixed the problem within 72 hours of discovering it, and that the company has added additional detection to protect against these types of authentication bypasses going forward.
Anu Yamunan, director of abuse and safety protections at Google Workspace, told KrebsOnSecurity the malicious activity began in late June, and involved “a few thousand” Workspace accounts that were created without being domain-verified.
Google Workspace offers a free trial that people can use to access services like Google Docs, but other services such as Gmail are only available to Workspace users who can validate control over the domain name associated with their email address. The weakness Google fixed allowed attackers to bypass this validation process. Google emphasized that none of the affected domains had previously been associated with Workspace accounts or services.
“The tactic here was to create a specifically-constructed request by a bad actor to circumvent email verification during the signup process,” Yamunan said. “The vector here is they would use one email address to try to sign in, and a completely different email address to verify a token. Once they were email verified, in some cases we have seen them access third party services using Google single sign-on.”
Yamunan said none of the potentially malicious workspace accounts were used to abuse Google services, but rather the attackers sought to impersonate the domain holder to other services online.
In the case of the reader who shared the breach notice from Google, the imposters used the authentication bypass to associate his domain with a Workspace account. And that domain was tied to his login at several third-party services online. Indeed, the alert this reader received from Google said the unauthorized Workspace account appears to have been used to sign in to his account at Dropbox.
Google said the now-fixed authentication bypass is unrelated to a recent issue involving cryptocurrency-based domain names that were apparently compromised in their transition to Squarespace, which last year acquired more than 10 million domains that were registered via Google Domains.
On July 12, a number of domains tied to cryptocurrency businesses were hijacked from Squarespace users who hadn’t yet set up their Squarespace accounts. Squarespace has since published a statement blaming the domain hijacks on “a weakness related to OAuth logins”, which Squarespace said it fixed within hours.
SN 984: CrowdStruck - Crowdstrike, Cellebrite, More Entrust
- Cellebrite unlocks Trump's would-be assassin's phone.
- Cisco reported on a CVSS of 10.0
- Entrust drops the other shoe
- Google gives up on removing 3rd-party cookies
- Miscellany
- Snowflake and data warehouse applications
- CDK auto dealership outage
- Polyfill.io and resource hashes
- MITM
- Blocking Copilot
- Blocking incoming connections via IP
- CrowdStruck
Show Notes - https://www.grc.com/sn/SN-984-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to this show at https://twit.tv/shows/security-now.
Get episodes ad-free with Club TWiT at https://twit.tv/clubtwit
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Sponsors:
Phish-Friendly Domain Registry “.top” Put on Notice
The Chinese company in charge of handing out domain names ending in “.top” has been given until mid-August 2024 to show that it has put in place systems for managing phishing reports and suspending abusive domains, or else forfeit its license to sell domains. The warning comes amid the release of new findings that .top was the most common suffix in phishing websites over the past year, second only to domains ending in “.com.”

Image: Shutterstock.
On July 16, the Internet Corporation for Assigned Names and Numbers (ICANN) sent a letter to the owners of the .top domain registry. ICANN has filed hundreds of enforcement actions against domain registrars over the years, but this is thought to be the first in which ICANN has singled out a domain registry responsible for maintaining an entire top-level domain (TLD).
Among other reasons, the missive chided the registry for failing to respond to reports about phishing attacks involving .top domains.
“Based on the information and records gathered through several weeks, it was determined that .TOP Registry does not have a process in place to promptly, comprehensively, and reasonably investigate and act on reports of DNS Abuse,” the ICANN letter reads (PDF).
ICANN’s warning redacted the name of the recipient, but records show the .top registry is operated by a Chinese entity called Jiangsu Bangning Science & Technology Co. Ltd. Representatives for the company have not responded to requests for comment.
Domains ending in .top were represented prominently in a new phishing report released today by the Interisle Consulting Group, which sources phishing data from several places, including the Anti-Phishing Working Group (APWG), OpenPhish, PhishTank, and Spamhaus.
Interisle’s newest study examined nearly two million phishing attacks in the last year, and found that phishing sites accounted for more than four percent of all new .top domains between May 2023 and April 2024. Interisle said .top has roughly 2.76 million domains in its stable, and that more than 117,000 of those were phishing sites in the past year.
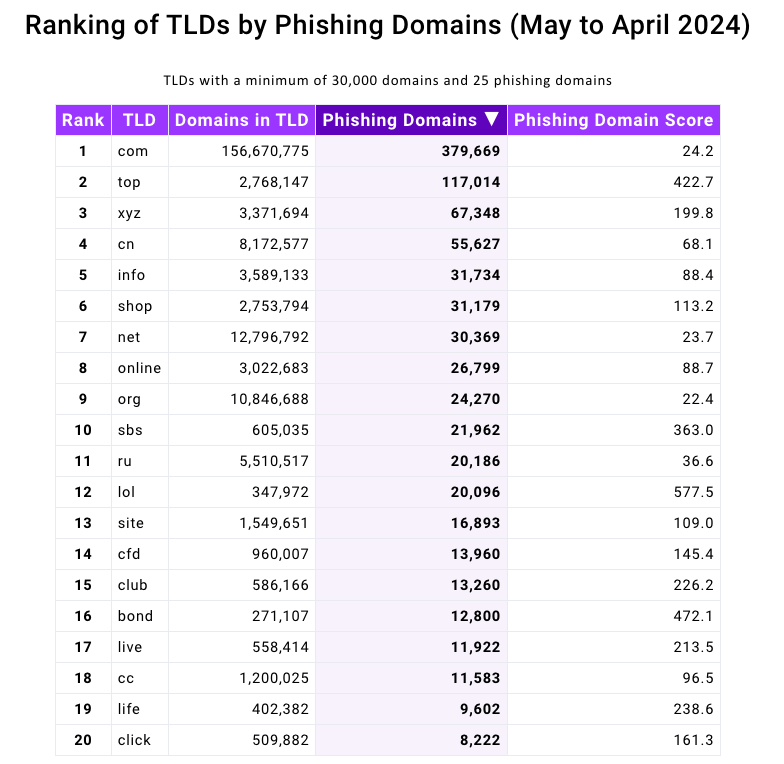
Source: Interisle Consulting Group.
ICANN said its review was based on information collected and studied about .top domains over the past few weeks. But the fact that high volumes of phishing sites are being registered through Jiangsu Bangning Science & Technology Co Ltd. is hardly a new trend.
For example, more than 10 years ago the same Chinese registrar was the fourth most common source of phishing websites, as tracked by the APWG. Bear in mind that the APWG report excerpted below was published more than a year before Jiangsu Bangning received ICANN approval to introduce and administer the new .top registry.
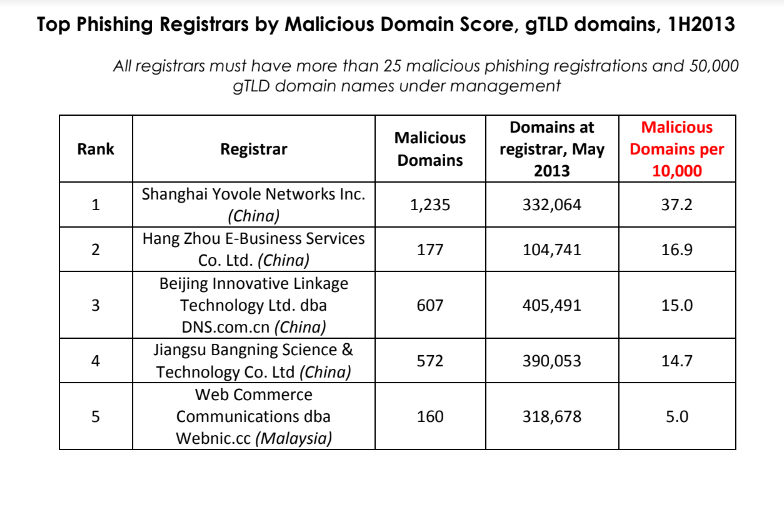
Source: APWG phishing report from 2013, two years before .top came into being.
A fascinating new wrinkle in the phishing landscape is the growth in scam pages hosted via the InterPlanetary File System (IPFS), a decentralized data storage and delivery network that is based on peer-to-peer networking. According to Interisle, the use of IPFS to host and launch phishing attacks — which can make phishing sites more difficult to take down — increased a staggering 1,300 percent, to roughly 19,000 phishing sites reported in the last year.
Last year’s report from Interisle found that domain names ending in “.us” — the top-level domain for the United States — were among the most prevalent in phishing scams. While .us domains are not even on the Top 20 list of this year’s study, “.com” maintained its perennial #1 spot as the largest source of phishing domains overall.
A year ago, the phishiest domain registrar by far was Freenom, a now-defunct registrar that handed out free domains in several country-code TLDs, including .tk, .ml, .ga and .cf. Freenom went out of business after being sued by Meta, which alleged Freenom ignored abuse complaints while monetizing traffic to abusive domains.
Following Freenom’s demise, phishers quickly migrated to other new low-cost TLDs and to services that allow anonymous, free domain registrations — particularly subdomain services. For example, Interisle found phishing attacks involving websites created on Google’s blogspot.com skyrocketed last year more than 230 percent. Other subdomain services that saw a substantial growth in domains registered by phishers include weebly.com, github.io, wix.com, and ChangeIP, the report notes.
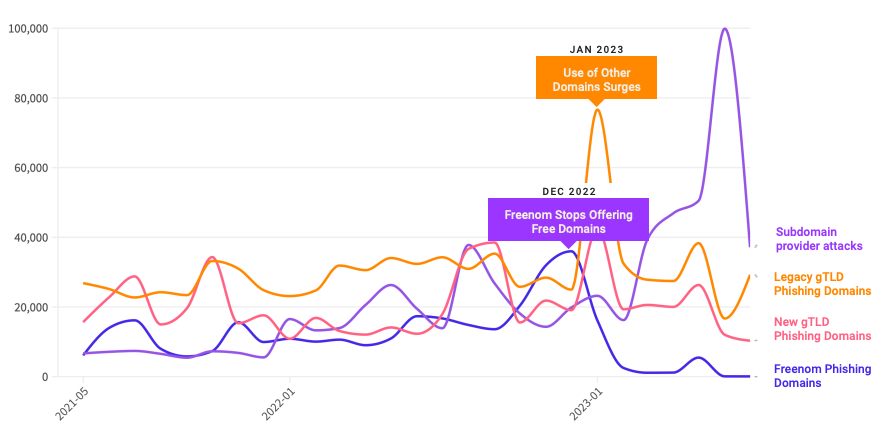
Source: Interisle Consulting.
Interisle Consulting partner Dave Piscitello said ICANN could easily send similar warning letters to at least a half-dozen other top-level domain registries, noting that spammers and phishers tend to cycle through the same TLDs periodically — including .xyz, .info, .support and .lol, all of which saw considerably more business from phishers after Freenom’s implosion.
Piscitello said domain registrars and registries could significantly reduce the number of phishing sites registered through their services just by flagging customers who try to register huge volumes of domains at once. Their study found that at least 27% of the domains used for phishing were registered in bulk — i.e. the same registrant paid for hundreds or thousands of domains in quick succession.
The report includes a case study in which a phisher this year registered 17,562 domains over the course of an eight-hour period — roughly 38 domains per minute — using .lol domains that were all composed of random letters.
ICANN tries to resolve contract disputes privately with the registry and registrar community, and experts say the nonprofit organization usually only publishes enforcement letters when the recipient is ignoring its private notices. Indeed, ICANN’s letter notes Jiangsu Bangning didn’t even open its emailed notifications. It also cited the registry for falling behind in its ICANN membership fees.
With that in mind, a review of ICANN’s public enforcement activity suggests two trends: One is that there have been far fewer public compliance and enforcement actions in recent years — even as the number of new TLDs has expanded dramatically.
The second is that in a majority of cases, the failure of a registry or registrar to pay its annual ICANN membership fees was cited as a reason for a warning letter. A review of nearly two dozen enforcement letters ICANN has sent to domain registrars since 2022 shows that failure to pay dues was cited as a reason (or the reason) for the violation at least 75 percent of the time.
Piscitello, a former ICANN board member, said nearly all breach notices sent out while he was at ICANN were because the registrar owed money.
“I think the rest is just lipstick to suggest that ICANN’s on top of DNS Abuse,” Piscitello said.
KrebsOnSecurity has sought comment from ICANN and will update this story if they respond.
TWiT 989: Executive Laundry Folding Disorder - Crowdstrike, Prime Day, Stremaing the Olympics
- Biden drops out of the race via tweet
- "CrowdStrike update that caused global outage likely skipped checks, experts say
- Amazon's Prime Day causes worker injuries, Senate probe finds
- Kaspersky Lab Closing U.S. Division; Laying Off Workers
- Researchers: Weak Security Defaults Enabled Squarespace Domains Hijacks
- The Paris Olympics Will Show Us the Future of Sports on TV
- Judge dismisses much of SEC suit against SolarWinds over cybersecurity disclosures
- FBI Used New Cellebrite Software to Access Trump Shooter's Phone
- Hundreds more Californians get housing with Apple's help
- Microsoft's new AI system 'SpreadsheetLLM' unlocks insights from spreadsheets, boosting enterprise productivity
- Bethesda Game Studios workers unionize under Communications Workers of America
Host: Leo Laporte
Guests: Lisa Schmeiser, Ashley Esqueda, and Anthony Ha
Download or subscribe to this show at https://twit.tv/shows/this-week-in-tech
Get episodes ad-free with Club TWiT at https://twit.tv/clubtwit
Sponsors:
Why the Crowdstrike Outage is a Golden Opportunity for MSPs
Leverage the Crowdstrike outage to position your MSP as a business continuity expert. Use timely, relevant content from our extensive MSP library to attract new clients.
Source: Why the Crowdstrike Outage is a Golden Opportunity for MSPs - Technibble.com
Global Microsoft Meltdown Tied to Bad Crowstrike Update
A faulty software update from cybersecurity vendor Crowdstrike crippled countless Microsoft Windows computers across the globe today, disrupting everything from airline travel and financial institutions to hospitals and businesses online. Crowdstrike said a fix has been deployed, but experts say the recovery from this outage could take some time, as Crowdstrike’s solution needs to be applied manually on a per-machine basis.

A photo taken at San Jose International Airport today shows the dreaded Microsoft “Blue Screen of Death” across the board. Credit: Twitter.com/adamdubya1990
Earlier today, an errant update shipped by Crowdstrike began causing Windows machines running the software to display the dreaded “Blue Screen of Death,” rendering those systems temporarily unusable. Like most security software, Crowdstrike requires deep hooks into the Windows operating system to fend off digital intruders, and in that environment a tiny coding error can quickly lead to catastrophic outcomes.
In a post on Twitter/X, Crowdstrike CEO George Kurtz said an update to correct the coding mistake has been shipped, and that Mac and Linux systems are not affected.
“This is not a security incident or cyberattack,” Kurtz said on Twitter, echoing a written statement by Crowdstrike. “The issue has been identified, isolated and a fix has been deployed.”
Posting to Twitter/X, the director of Crowdstrike’s threat hunting operations said the fix involves booting Windows into Safe Mode or the Windows Recovery Environment (Windows RE), deleting the file “C-00000291*.sys” and then restarting the machine.
The software snafu may have been compounded by a recent series of outages involving Microsoft’s Azure cloud services, The New York Times reports, although it remains unclear whether those Azure problems are at all related to the bad Crowdstrike update.

A reader shared this photo taken earlier today at Denver International Airport. Credit: Twitter.com/jterryy07
Reactions to today’s outage were swift and brutal on social media, which was flooded with images of people at airports surrounded by computer screens displaying the Microsoft blue screen error. Many Twitter/X users chided the Crowdstrike CEO for failing to apologize for the massively disruptive event, while others noted that doing so could expose the company to lawsuits.
Meanwhile, the international Windows outage quickly became the most talked-about subject on Twitter/X, whose artificial intelligence bots collated a series of parody posts from cybersecurity professionals pretending to be on their first week of work at Crowdstrike. Incredibly,Twitter/X’s AI summarized these sarcastic posts into a sunny, can-do story about Crowdstrike that was promoted as the top discussion on Twitter this morning.
“Several individuals have recently started working at the cybersecurity firm Crowdstrike and have expressed their excitement and pride in their new roles,” the AI summary read. “They have shared their experiences of pushing code to production on their first day and are looking forward to positive outcomes in their work.”
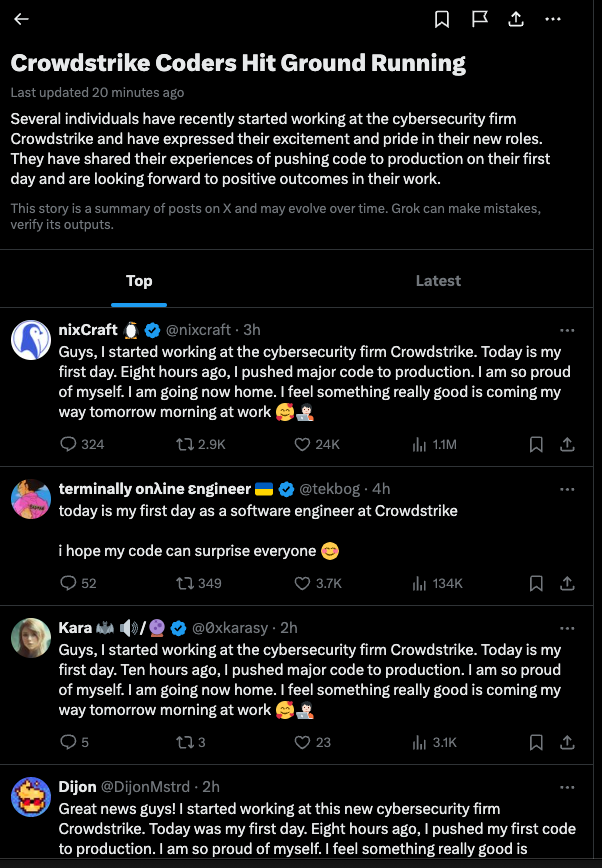
The top story today on Twitter/X, as brilliantly summarized by X’s AI bots.
Wired.com’s Matt Burgess writes that within health care and emergency services, various medical providers around the world have reported issues with their Windows-linked systems, sharing news on social media or their own websites.
“The US Emergency Alert System, which issues hurricane warnings, said that there had been various 911 outages in a number of states,” Burgess wrote. “Germany’s University Hospital Schleswig-Holstein said it was canceling some nonurgent surgeries at two locations. In Israel, more than a dozen hospitals have been impacted, as well as pharmacies, with reports saying ambulances have been rerouted to nonimpacted medical organizations.”
In the United Kingdom, NHS England has confirmed that appointment and patient record systems have been impacted by the outages.
“One hospital has declared a ‘critical’ incident after a third-party IT system it used was impacted,” Wired reports. “Also in the country, train operators have said there are delays across the network, with multiple companies being impacted.”
This is an evolving story. Stay tuned for updates.
The Linux Link Tech Show Episode 1060
SN 983: A Snowflake's Chance - CDN Safety, Microsoft's Behavior, CDK Ransomware Attack
- Using Content Delivery Networks Safely
- The CDK Global Ransomware Attack
- The IRS and Entrust
- Polyfill.io fallout
- Microsoft's Behavior
- A Snowflake's Chance
Show Notes - https://www.grc.com/sn/SN-983-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to this show at https://twit.tv/shows/security-now.
Get episodes ad-free with Club TWiT at https://twit.tv/clubtwit
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Sponsors:
Researchers: Weak Security Defaults Enabled Squarespace Domains Hijacks
At least a dozen organizations with domain names at domain registrar Squarespace saw their websites hijacked last week. Squarespace bought all assets of Google Domains a year ago, but many customers still haven’t set up their new accounts. Experts say malicious hackers learned they could commandeer any migrated Squarespace accounts that hadn’t yet been registered, merely by supplying an email address tied to an existing domain.
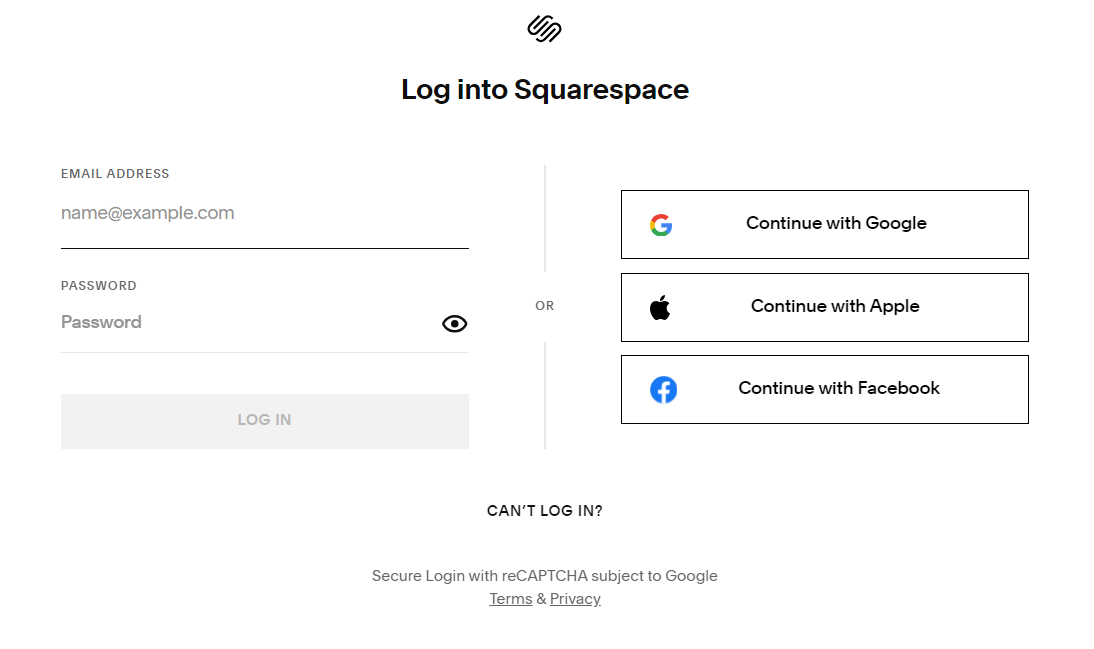
Until this past weekend, Squarespace’s website had an option to log in via email.
The Squarespace domain hijacks, which took place between July 9 and July 12, appear to have mostly targeted cryptocurrency businesses, including Celer Network, Compound Finance, Pendle Finance, and Unstoppable Domains. In some cases, the attackers were able to redirect the hijacked domains to phishing sites set up to steal visitors’ cryptocurrency funds.
New York City-based Squarespace purchased roughly 10 million domain names from Google Domains in June 2023, and it has been gradually migrating those domains to its service ever since. Squarespace has not responded to a request for comment, nor has it issued a statement about the attacks.
But an analysis released by security experts at Metamask and Paradigm finds the most likely explanation for what happened is that Squarespace assumed all users migrating from Google Domains would select the social login options — such “Continue with Google” or “Continue with Apple” — as opposed to the “Continue with email” choice.
Taylor Monahan, lead product manager at Metamask, said Squarespace never accounted for the possibility that a threat actor might sign up for an account using an email associated with a recently-migrated domain before the legitimate email holder created the account themselves.
“Thus nothing actually stops them from trying to login with an email,” Monahan told KrebsOnSecurity. “And since there’s no password on the account, it just shoots them to the ‘create password for your new account’ flow. And since the account is half-initialized on the backend, they now have access to the domain in question.”
Sometime in the last 24 hours, Squarespace removed the ability for people to create an account with just an email address. That option was available when KrebsOnSecurity created a test Squarespace account on Saturday (it’s unclear whether Squarespace ever sent a confirmation email from that signup, but I still haven’t received one).
What’s more, Monahan said, Squarespace did not require email verification for new accounts created with a password.
“The domains being migrated from Google to Squarespace are known,” Monahan said. “It’s either public or easily discernible info which email addresses have admin of a domain. And if that email never sets up their account on Squarespace — say because the billing admin left the company five years ago or folks just ignored the email — anyone who enters that email@domain in the squarespace form now has full access to control to the domain.”
The researchers say some Squarespace domains that were migrated over also could be hijacked if attackers discovered the email addresses for less privileged user accounts tied to the domain, such as “domain manager,” which likewise has the ability to transfer a domain or point it to a different Internet address.

Squarespace says domain owners and domain managers have many of the same privileges, including the ability to move a domain or manage the site’s domain name server (DNS) settings.
Monahan said the migration has left domain owners with fewer options to secure and monitor their accounts.
“Squarespace can’t support users who need any control or insight into the activity being performed in their account or domain,” Monahan said. “You basically have no control over the access different folks have. You don’t have any audit logs. You don’t get email notifications for some actions. The owner doesn’t get email notification for actions taken by a ‘domain manager.’ This is absolutely insane if you’re used to and expecting the controls Google provides.”
The researchers have published a comprehensive guide for locking down Squarespace user accounts, which urges Squarespace users to enable multi-factor authentication (disabled during the migration).
“Determining what emails have access to your new Squarespace account is step 1,” the help guide advises. “Most teams DO NOT REALIZE these accounts even exist, let alone theoretically have access.”
The guide also recommends removing unnecessary Squarespace user accounts, and disabling reseller access in Google Workspace.
“If you bought Google Workspace via Google Domains, Squarespace is now your authorized reseller,” the help document explains. “This means that anyone with access to your Squarespace account also has a backdoor into your Google Workspace unless you explicitly disable it by following the instructions here, which you should do. It’s easier to secure one account than two.”
TWiT 988: Flaming Corn Maze - AT&T Breach, Galaxy Z Fold6, Olympic Disinfo
- Galaxy Z Fold 6 launches for $1,899 with wider displays
- FTC bans anonymous messaging app NGL from hosting children
- AT&T says criminals stole phone records of 'nearly all' customers in new data breach
- EU accuses Elon Musk's X of deceptive practices over blue 'checkmark'
- After 41 years Microsoft quietly adds spellchecking and autocorrect to Windows Notepad
- AI PCs: Qualcomm (QCOM), Microsoft (MSFT) Turn to AI to Revive PC Market
- Goldman Sachs: AI Is Overhyped, Wildly Expensive, and Unreliable
- U.S. says Russian bot farm used AI to impersonate Americans
- Disinfo spreaders set their sights on Paris Olympics
- My 28,000-follower Twitter account was hacked—and it changed my life for the better
- Is anyone concerned that Palmer Luckey's new compay Anduril (aka Aragorn's sword from LOTR) is making military products and has a mission statement straight out of Robocop?
- Apple now makes it easier to switch from Google Photos to iCloud Photos
- FTC Fires A Warning Shot At Eight Companies Over 'Right To Repair' Violations
Host: Leo Laporte
Guests: Mike Elgan, Denise Howell, and Harry McCracken
Download or subscribe to this show at https://twit.tv/shows/this-week-in-tech
Get episodes ad-free with Club TWiT at https://twit.tv/clubtwit
Sponsors:
Crooks Steal Phone, SMS Records for Nearly All AT&T Customers
AT&T Corp. disclosed today that a new data breach has exposed phone call and text message records for roughly 110 million people — nearly all of its customers. AT&T said it delayed disclosing the incident in response to “national security and public safety concerns,” noting that some of the records included data that could be used to determine where a call was made or text message sent. AT&T also acknowledged the customer records were exposed in a cloud database that was protected only by a username and password (no multi-factor authentication needed).

In a regulatory filing with the U.S. Securities and Exchange Commission today, AT&T said cyber intruders accessed an AT&T workspace on a third-party cloud platform in April, downloading files containing customer call and text interactions between May 1 and October 31, 2022, as well as on January 2, 2023.
The company said the stolen data includes records of calls and texts for mobile providers that resell AT&T’s service, but that it does not include the content of calls or texts, Social Security numbers, dates of birth, or any other personally identifiable information.
However, the company said a subset of stolen records included information about the location of cellular communications towers closest to the subscriber, data that could be used to determine the approximate location of the customer device initiating or receiving those text messages or phone calls.
“While the data does not include customer names, there are often ways, using publicly available online tools, to find the name associated with a specific telephone number,” AT&T allowed.
AT&T’s said it learned of the breach on April 19, but delayed disclosing it at the request of federal investigators. The company’s SEC disclosure says at least one individual has been detained by the authorities in connection with the breach.
In a written statement shared with KrebsOnSecurity, the FBI confirmed that it asked AT&T to delay notifying affected customers.
“Shortly after identifying a potential breach to customer data and before making its materiality decision, AT&T contacted the FBI to report the incident,” the FBI statement reads. “In assessing the nature of the breach, all parties discussed a potential delay to public reporting under Item 1.05(c) of the SEC Rule, due to potential risks to national security and/or public safety. AT&T, FBI, and DOJ worked collaboratively through the first and second delay process, all while sharing key threat intelligence to bolster FBI investigative equities and to assist AT&T’s incident response work.”
Techcrunch quoted an AT&T spokesperson saying the customer data was stolen as a result of a still-unfolding data breach involving more than 160 customers of the cloud data provider Snowflake.
Earlier this year, malicious hackers figured out that many major companies have uploaded massive amounts of valuable and sensitive customer data to Snowflake servers, all the while protecting those Snowflake accounts with little more than a username and password.
Wired reported last month how the hackers behind the Snowflake data thefts purchased stolen Snowflake credentials from dark web services that sell access to usernames, passwords and authentication tokens that are siphoned by information-stealing malware. For its part, Snowflake says it now requires all new customers to use multi-factor authentication.
Other companies with millions of customer records stolen from Snowflake servers include Advance Auto Parts, Allstate, Anheuser-Busch, Los Angeles Unified, Mitsubishi, Neiman Marcus, Progressive, Pure Storage, Santander Bank, State Farm, and Ticketmaster.
Earlier this year, AT&T reset passwords for millions of customers after the company finally acknowledged a data breach from 2018 involving approximately 7.6 million current AT&T account holders and roughly 65.4 million former account holders.
Mark Burnett is an application security architect, consultant and author. Burnett said the only real use for the data stolen in the most recent AT&T breach is to know who is contacting whom and how many times.
“The most concerning thing to me about this AT&T breach of ALL customer call and text records is that this isn’t one of their main databases; it is metadata on who is contacting who,” Burnett wrote on Mastodon. “Which makes me wonder what would call logs without timestamps or names have been used for.”
It remains unclear why so many major corporations persist in the belief that it is somehow acceptable to store so much sensitive customer data with so few security protections. For example, Advance Auto Parts said the data exposed included full names, Social Security numbers, drivers licenses and government issued ID numbers on 2.3 million people who were former employees or job applicants.
That may be because, apart from the class-action lawsuits that invariably ensue after these breaches, there is little holding companies accountable for sloppy security practices. AT&T told the SEC it does not believe this incident is likely to materially impact AT&T’s financial condition or results of operations. AT&T reported revenues of more than $30 billion in its most recent quarter.
The Stark Truth Behind the Resurgence of Russia’s Fin7
The Russia-based cybercrime group dubbed “Fin7,” known for phishing and malware attacks that have cost victim organizations an estimated $3 billion in losses since 2013, was declared dead last year by U.S. authorities. But experts say Fin7 has roared back to life in 2024 — setting up thousands of websites mimicking a range of media and technology companies — with the help of Stark Industries Solutions, a sprawling hosting provider that is a persistent source of cyberattacks against enemies of Russia.
In May 2023, the U.S. attorney for Washington state declared “Fin7 is an entity no more,” after prosecutors secured convictions and prison sentences against three men found to be high-level Fin7 hackers or managers. This was a bold declaration against a group that the U.S. Department of Justice described as a criminal enterprise with more than 70 people organized into distinct business units and teams.
The first signs of Fin7’s revival came in April 2024, when Blackberry wrote about an intrusion at a large automotive firm that began with malware served by a typosquatting attack targeting people searching for a popular free network scanning tool.
Now, researchers at security firm Silent Push say they have devised a way to map out Fin7’s rapidly regrowing cybercrime infrastructure, which includes more than 4,000 hosts that employ a range of exploits, from typosquatting and booby-trapped ads to malicious browser extensions and spearphishing domains.
Silent Push said it found Fin7 domains targeting or spoofing brands including American Express, Affinity Energy, Airtable, Alliant, Android Developer, Asana, Bitwarden, Bloomberg, Cisco (Webex), CNN, Costco, Dropbox, Grammarly, Google, Goto.com, Harvard, Lexis Nexis, Meta, Microsoft 365, Midjourney, Netflix, Paycor, Quickbooks, Quicken, Reuters, Regions Bank Onepass, RuPay, SAP (Ariba), Trezor, Twitter/X, Wall Street Journal, Westlaw, and Zoom, among others.
Zach Edwards, senior threat analyst at Silent Push, said many of the Fin7 domains are innocuous-looking websites for generic businesses that sometimes include text from default website templates (the content on these sites often has nothing to do with the entity’s stated business or mission).
Edwards said Fin7 does this to “age” the domains and to give them a positive or at least benign reputation before they’re eventually converted for use in hosting brand-specific phishing pages.
“It took them six to nine months to ramp up, but ever since January of this year they have been humming, building a giant phishing infrastructure and aging domains,” Edwards said of the cybercrime group.
In typosquatting attacks, Fin7 registers domains that are similar to those for popular free software tools. Those look-alike domains are then advertised on Google so that sponsored links to them show up prominently in search results, which is usually above the legitimate source of the software in question.
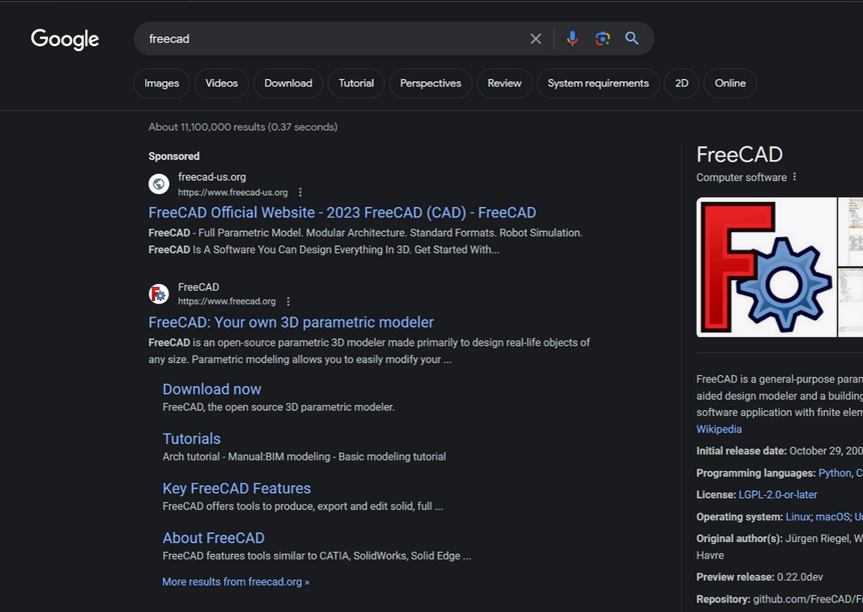
A malicious site spoofing FreeCAD showed up prominently as a sponsored result in Google search results earlier this year.
According to Silent Push, the software currently being targeted by Fin7 includes 7-zip, PuTTY, ProtectedPDFViewer, AIMP, Notepad++, Advanced IP Scanner, AnyDesk, pgAdmin, AutoDesk, Bitwarden, Rest Proxy, Python, Sublime Text, and Node.js.
In May 2024, security firm eSentire warned that Fin7 was spotted using sponsored Google ads to serve pop-ups prompting people to download phony browser extensions that install malware. Malwarebytes blogged about a similar campaign in April, but did not attribute the activity to any particular group.
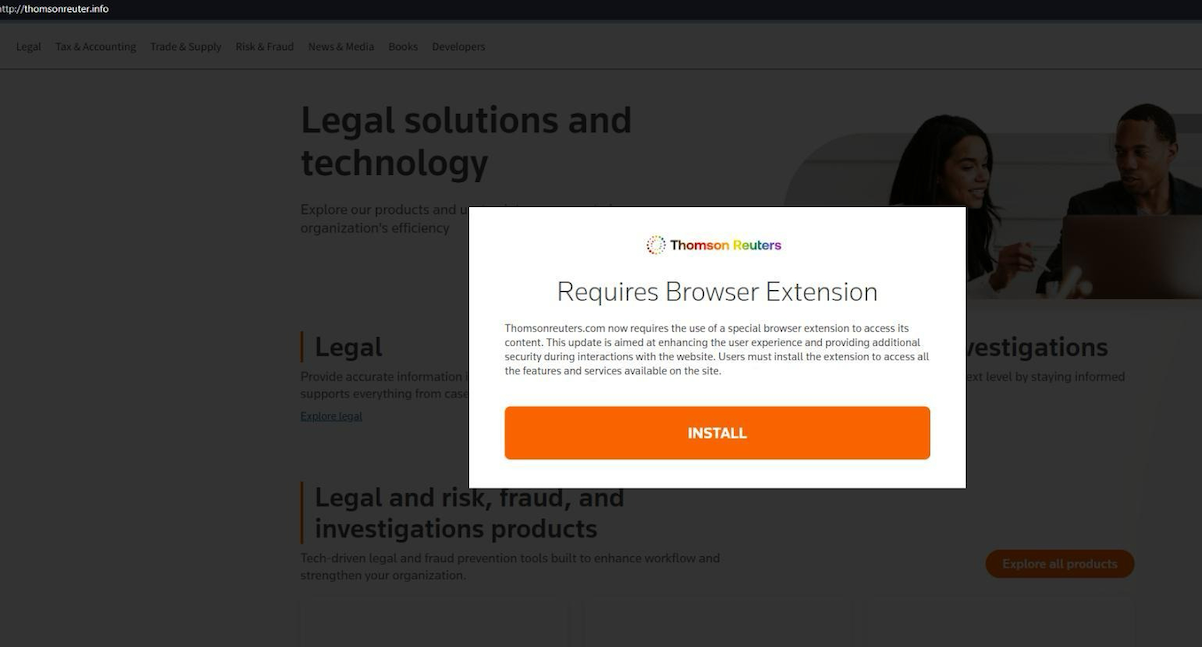
A pop-up at a Thomson Reuters typosquatting domain telling visitors they need to install a browser extension to view the news content.
Edwards said Silent Push discovered the new Fin7 domains after a hearing from an organization that was targeted by Fin7 in years past and suspected the group was once again active. Searching for hosts that matched Fin7’s known profile revealed just one active site. But Edwards said that one site pointed to many other Fin7 properties at Stark Industries Solutions, a large hosting provider that materialized just two weeks before Russia invaded Ukraine.
As KrebsOnSecurity wrote in May, Stark Industries Solutions is being used as a staging ground for wave after wave of cyberattacks against Ukraine that have been tied to Russian military and intelligence agencies.
“FIN7 rents a large amount of dedicated IP on Stark Industries,” Edwards said. “Our analysts have discovered numerous Stark Industries IPs that are solely dedicated to hosting FIN7 infrastructure.”
Fin7 once famously operated behind fake cybersecurity companies — with names like Combi Security and Bastion Secure — which they used for hiring security experts to aid in ransomware attacks. One of the new Fin7 domains identified by Silent Push is cybercloudsec[.]com, which promises to “grow your business with our IT, cyber security and cloud solutions.”
The fake Fin7 security firm Cybercloudsec.
Like other phishing groups, Fin7 seizes on current events, and at the moment it is targeting tourists visiting France for the Summer Olympics later this month. Among the new Fin7 domains Silent Push found are several sites phishing people seeking tickets at the Louvre.
“We believe this research makes it clear that Fin7 is back and scaling up quickly,” Edwards said. “It’s our hope that the law enforcement community takes notice of this and puts Fin7 back on their radar for additional enforcement actions, and that quite a few of our competitors will be able to take this pool and expand into all or a good chunk of their infrastructure.”
Further reading:
Stark Industries Solutions: An Iron Hammer in the Cloud.
A 2022 deep dive on Fin7 from the Swiss threat intelligence firm Prodaft (PDF).
SN 982: The Polyfill.io Attack - Entrust Responds, Passkey Redaction Attacks
- Entrust Responds
- Other major Certificate Authorities respond
- Passkey Redaction Attacks
- Syncing passkeys
- Port Knocking
- Fail2Ban
- The Polyfill.io Attack
Show Notes - https://www.grc.com/sn/SN-982-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to this show at https://twit.tv/shows/security-now.
Get episodes ad-free with Club TWiT at https://twit.tv/clubtwit
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Sponsors:
Microsoft Patch Tuesday, July 2024 Edition
Microsoft Corp. today issued software updates to plug at least 139 security holes in various flavors of Windows and other Microsoft products. Redmond says attackers are already exploiting at least two of the vulnerabilities in active attacks against Windows users.

The first Microsoft zero-day this month is CVE-2024-38080, a bug in the Windows Hyper-V component that affects Windows 11 and Windows Server 2022 systems. CVE-2024-38080 allows an attacker to increase their account privileges on a Windows machine. Although Microsoft says this flaw is being exploited, it has offered scant details about its exploitation.
The other zero-day is CVE-2024-38112, which is a weakness in MSHTML, the proprietary engine of Microsoft’s Internet Explorer web browser. Kevin Breen, senior director of threat research at Immersive Labs, said exploitation of CVE-2024-38112 likely requires the use of an “attack chain” of exploits or programmatic changes on the target host, a la Microsoft’s description: “Successful exploitation of this vulnerability requires an attacker to take additional actions prior to exploitation to prepare the target environment.”
“Despite the lack of details given in the initial advisory, this vulnerability affects all hosts from Windows Server 2008 R2 onwards, including clients,” Breen said. “Due to active exploitation in the wild this one should be prioritized for patching.”
Satnam Narang, senior staff research engineer at Tenable, called special attention to CVE-2024-38021, a remote code execution flaw in Microsoft Office. Attacks on this weakness would lead to the disclosure of NTLM hashes, which could be leveraged as part of an NTLM relay or “pass the hash” attack, which lets an attacker masquerade as a legitimate user without ever having to log in.
“One of the more successful attack campaigns from 2023 used CVE-2023-23397, an elevation of privilege bug in Microsoft Outlook that could also leak NTLM hashes,” Narang said. “However, CVE-2024-38021 is limited by the fact that the Preview Pane is not an attack vector, which means that exploitation would not occur just by simply previewing the file.”
In last month’s Patch Tuesday, Microsoft fixed a flaw in its Windows WiFi driver that attackers could use to install malicious software just by sending a vulnerable Windows host a specially crafted data packet over a local network. Jason Kikta at Automox said this month’s CVE-2024-38053 — a security weakness in Windows Layer Two Bridge Network — is another local network “ping-of-death” vulnerability that should be a priority for road warriors to patch.
“This requires close access to a target,” Kikta said. “While that precludes a ransomware actor in Russia, it is something that is outside of most current threat models. This type of exploit works in places like shared office environments, hotels, convention centers, and anywhere else where unknown computers might be using the same physical link as you.”
Automox also highlighted three vulnerabilities in Windows Remote Desktop a service that allocates Client Access Licenses (CALs) when a client connects to a remote desktop host (CVE-2024-38077, CVE-2024-38074, and CVE-2024-38076). All three bugs have been assigned a CVSS score of 9.8 (out of 10) and indicate that a malicious packet could trigger the vulnerability.
Tyler Reguly at Forta noted that today marks the End of Support date for SQL Server 2014, a platform that according to Shodan still has ~110,000 instances publicly available. On top of that, more than a quarter of all vulnerabilities Microsoft fixed this month are in SQL server.
“A lot of companies don’t update quickly, but this may leave them scrambling to update those environments to supported versions of MS-SQL,” Reguly said.
It’s a good idea for Windows end-users to stay current with security updates from Microsoft, which can quickly pile up otherwise. That doesn’t mean you have to install them on Patch Tuesday. Indeed, waiting a day or three before updating is a sane response, given that sometimes updates go awry and usually within a few days Microsoft has fixed any issues with its patches. It’s also smart to back up your data and/or image your Windows drive before applying new updates.
For a more detailed breakdown of the individual flaws addressed by Microsoft today, check out the SANS Internet Storm Center’s list. For those admins responsible for maintaining larger Windows environments, it often pays to keep an eye on Askwoody.com, which frequently points out when specific Microsoft updates are creating problems for a number of users.
As ever, if you experience any problems applying any of these updates, consider dropping a note about it in the comments; chances are decent someone else reading here has experienced the same issue, and maybe even has a solution.
Rust leaps forward in language popularity index
Rust has leaped to its highest position ever in the monthly Tiobe index of language popularity, scaling to the 13th spot this month, with placement in the top 10 anticipated in an upcoming edition.
Previously, Rust has never gone higher than 17th place in the Tiobe Programming Index. Tiobe CEO Paul Jansen attributed Rust’s ascent in the just-released July index to a February 2024 US White House report recommending Rust over C/C+, for safety reasons. He also credited the growing community and ecosystem support for the language. “Rust is finally moving up. After the tailwind of the US government, which recently announced to recommend moving from C/C++ to Rust for security reasons, things are going fast for Rust,” Jansen said. “The community is growing, including the number of third-party libraries and tools. In short, Rust is preparing itself for a top 10 position in the Tiobe index.”
FTC’s non-compete ban almost certainly dead, based on a Texas federal court decision
In a highly-anticipated federal ruling on July 3, US District Court Judge Ada Brown determined that the US Federal Trade Commission (FTC) did not have the authority to issue a nationwide ban of non-compete agreements. Although the judge’s decision was preliminary, employment lawyers watching the case agree that the FTC non-compete move is effectively dead.
Brown, of the US District Court for the Northern District of Texas, said that she would issue a final ruling on Aug. 30, the day before the FTC ban was slated to take effect. But based on the strong wording of her preliminary decision, there seemed little doubt that she would ultimately block the ban.
Researchers reveal flaws in AI agent benchmarking
As agents using artificial intelligence have wormed their way into the mainstream for everything from customer service to fixing software code, it’s increasingly important to determine which are the best for a given application, and the criteria to consider when selecting an agent besides its functionality. And that’s where benchmarking comes in.
Benchmarks don’t reflect real-world applicationsHowever, a new research paper, AI Agents That Matter, points out that current agent evaluation and benchmarking processes contain a number of shortcomings that hinder their usefulness in real-world applications. The authors, five Princeton University researchers, note that those shortcomings encourage development of agents that do well in benchmarks, but not in practice, and propose ways to address them.
8 reasons developers love Go—and 8 reasons they don't
In 2007, some of the programmers at Google looked at their options for writing software and didn’t like what they saw. They needed to manage millions of lines of code that would be constantly storing and shipping data for the world wide web. The code would juggle thousands or maybe millions of connections on networks throughout the globe. The data paths were full of challenges from race cases and concurrency.
The existing programming languages weren’t much help. They were built for games or managing desktops, or many of the other common tasks from a world before the web browser. Their rough edges and failure modes drove coders at Google crazy enough to start asking if there might be a better way. Was there something that could handle the I/O chores in just a few lines with all of the safety and security that Google needed?
AI’s moment of disillusionment
Well, that didn’t take long. After all the “this time it’s different” comments about artificial intelligence (We see you, John Chambers!), enterprises are coming to grips with reality. AI isn’t going to take your job. It’s not going to write your code. It’s not going to write all your marketing copy (not unless you’re prepared to hire back the humans to fix it). And, no, it’s nowhere near artificial general intelligence (AGI) and won’t be anytime soon. Possibly never.