You are here
Technology
TWiT 987: Often Plagiarized, Never Equalled - Sapce Junk, Threads Hits 175M Users, AIndependence
- Why Surgeon General's Social Media Warning Label is a Bad Idea
- Russia says Apple blocks 25 VPN apps in Russia, IFX reports
- Microsoft MSFT Tells Texas Agencies They Were Exposed in Russian Hack
- Microsoft says it's okay to steal content published on the web
- Declare your AIndependence: block AI bots, scrapers and crawlers with a single click
- Perplexity's grand theft AI
- The Julian Assange Saga Is Finally Over
- Zotac's Big Mistake | Consumer Warranty & Business Data Exposure
- NASA and SpaceX misjudged the risks from reentering space junk
- The White House will host a conference for social media creators
- Meta's Threads hits 175 million users one year after launch
- Google emissions jump nearly 50% over five years as AI use surges
- Judge blocks Mississippi law that required age verification on social media
Host: Leo Laporte
Guests: Paris Martineau, Allyn Malventano, and Larry Magid
Download or subscribe to this show at https://twit.tv/shows/this-week-in-tech
Get episodes ad-free with Club TWiT at https://twit.tv/clubtwit
Sponsors:
The next 10 years for cloud computing
The landscape of cloud computing is changing significantly as enterprises question the value of public cloud solutions. This shift marks a departure from previous years when the public cloud was widely regarded as the panacea for all technology and infrastructure needs. Companies are now reconsidering the efficacy, cost efficiency, and strategic alignment of public cloud computing in their IT frameworks. We’ve also been discussing this topic here in recent years.
What’s new in MySQL 9.0
Oracle celebrated the beginning of July with the general availability of three releases of its open source database, MySQL: MySQL 8.0.38, the first update of its long-term support (LTS) version, MySQL 8.4, and the first major version of its 9.x innovation release, MySQL 9.0.
While the v8 releases are bug fixes and security releases only, MySQL 9.0 Innovation is a shiny new version with additional features, as well as some changes that may require attention when upgrading from a previous version.
The new 9.0 versions of MySQL Clients, Tools, and Connectors are also live, and Oracle recommends that they be used with MySQL Server 8.0, and 8.4 LTS as well as with 9.0 Innovation.
How to use Refit to consume APIs in ASP.NET Core
Refit is an open-source library for .NET, .NET Core, and Xamarin that makes consuming REST APIs simpler and easier by enabling you to define the API endpoints as C# interfaces, thereby eliminating the need to create HTTP requests and parse HTTP responses manually.
In this article we will delve into the Refit library for .NET and see first-hand how it simplifies the development of APIs. To use the code examples provided in this article, you should have Visual Studio 2022 installed in your system. If you don’t already have a copy, you can download Visual Studio 2022 here.
Visual Studio Code previews incoming/outgoing changes graph
The latest update of Visual Studio Code is previewing an alternative visualization of incoming and outgoing changes. The update also includes a new tool that enhances environment discovery for Python installations.
Introduced July 3, Visual Studio Code 1.91, also known as the June 2024 release of the editor, can be downloaded for Windows, Linux, and macOS at code.visualstudio.com.
The experimental incoming/outgoing changes graph provides a graph view of the current branch, the current branch’s upstream branch, and an optional base branch. The root of the graph is the common ancestor of these branches. Users can enable the new visualization with the scm.experimental.showHistoryGraph setting.
Understanding DiskANN, a foundation of the Copilot Runtime
One of the key components of Microsoft’s Copilot Runtime edge AI development platform for Windows is a new vector search technology, DiskANN (Disk Accelerated Nearest Neighbors). Building on a long-running Microsoft Research project, DiskANN is a way of building and managing vector indexes inside your applications. It uses a mix of in-memory and disk storage to map an in-memory quantized vector graph to a high-precision graph help on disk.
ECMAScript 2024 JavaScript standard approved
ECMAScript 2024, the latest version of ECMA International’s standard for JavaScript, has been officially approved, with features including transferring ArrayBuffers and advanced capabilities for working with string sets.
The ECMAScript 2024 specification, also generally known as ECMA-262, was approved on June 26. Among the features are added facilities for resizing and transferring ArrayBuffers and SharedArrayBuffers. ArrayBuffers have previously enabled in-memory handling of binary data. The new feature extends ArrayBuffer constructors to take an additional maximum length that allows in-place growth and shrinking of buffers. SharedArrayBuffer was also extended to take an additional maximum length that allows in-place growth.
JetBrains launches Qodana Self-Hosted
JetBrains has released an on-premises edition of Qodana, the company’s code quality platform based on the static code analysis engine of JetBrains IDEs. With Qodana Self-Hosted, users can manage and maintain the platform on their own infrastructure.
With Qodana Self-Hosted, announced July 3, developers gain complete control over analysis reports, user accounts, and other sensitive data, as well as Qodana maintenance and upgrades, JetBrains said. Qodana Self-Hosted offers a suite of features of the company’s advanced cloud plan, Qodana Ultimate Plus, that make static code analysis effective for organizations of any size, JetBrains said. The feature set includes an issues overview, integrations with JetBrains IDE and Visual Studio Code, quick fixes, CI/CD integrations, license auditing, rule-based custom code inspections, and other capabilities.
The Not-So-Secret Network Access Broker x999xx

Most accomplished cybercriminals go out of their way to separate their real names from their hacker handles. But among certain old-school Russian hackers it is not uncommon to find major players who have done little to prevent people from figuring out who they are in real life. A case study in this phenomenon is “x999xx,” the nickname chosen by a venerated Russian hacker who specializes in providing the initial network access to various ransomware groups.
x999xx is a well-known “access broker” who frequently sells access to hacked corporate networks — usually in the form of remote access credentials — as well as compromised databases containing large amounts of personal and financial data.
In an analysis published in February 2019, cyber intelligence firm Flashpoint called x999xx one of the most senior and prolific members of the top-tier Russian-language cybercrime forum Exploit, where x999xx could be seen frequently advertising the sale of stolen databases and network credentials.
In August 2023, x999xx sold access to a company that develops software for the real estate industry. In July 2023, x999xx advertised the sale of Social Security numbers, names, and birthdays for the citizenry of an entire U.S. state (unnamed in the auction).
A month earlier, x999xx posted a sales thread for 80 databases taken from Australia’s largest retail company. “You may use this data to demand a ransom or do something different with it,” x999xx wrote on Exploit. “Unfortunately, the flaw was patched fast. [+] no one has used the data yet [+] the data hasn’t been used to send spam [+] the data is waiting for its time.”
In October 2022, x999xx sold administrative access to a U.S. healthcare provider.
ALIAS: MAXNMThe oldest account by the name x999xx appeared in 2009 on the Russian language cybercrime forum Verified, under the email address maxnm@ozersk.com. Ozersk is a city in the Chelyabinsk region of west-central Russia.
According to the breach tracking service Constella Intelligence, the address maxnm@ozersk.com was used more than a decade ago to create an account at Vktontakte (the Russian answer to Facebook) under the name Maxim Kirtsov from Ozersk. Mr. Kirtsov’s profile — “maxnm” — says his birthday is September 5, 1991.

Personal photos Maxnm shared on Vktontakte in 2016. The caption has been machine translated from Russian.
The user x999xx registered on the Russian language cybercrime community Zloy in 2014 using the email address maxnmalias-1@yahoo.com. Constella says this email address was used in 2022 at the Russian shipping service cdek.ru in by a Maksim Georgievich Kirtsov from Ozersk.
Additional searches on these contact details reveal that prior to 2009, x999xx favored the handle Maxnm on Russian cybercrime forums. Cyber intelligence company Intel 471 finds the user Maxnm registered on Zloy in 2006 from an Internet address in Chelyabinsk, using the email address kirtsov@telecom.ozersk.ru.
That same email address was used to create Maxnm accounts on several other crime forums, including Spamdot and Exploit in 2005 (also from Chelyabinsk), and Damagelab in 2006.
A search in Constella for the Russian version of Kirtsov’s full name — Кирцов Максим Георгиевич — brings up multiple accounts registered to maksya@icloud.com.
A review of the digital footprint for maksya@icloud.com at osint.industries reveals this address was used a decade ago to register a still-active account at imageshack.com under the name x999xx. That account features numerous screenshots of financial statements from various banks, chat logs with other hackers, and even hacked websites.
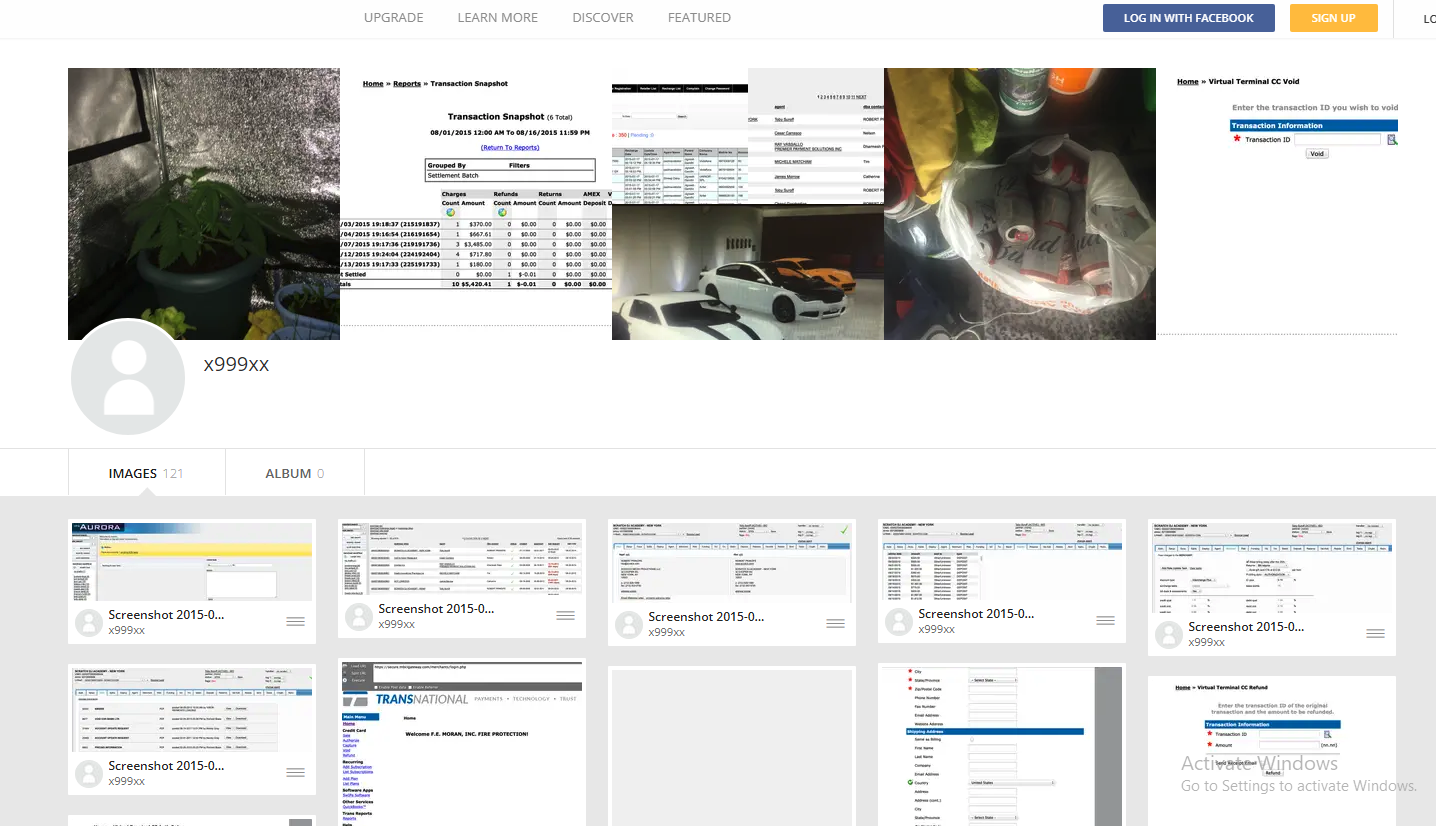
x999xx’s Imageshack account includes screenshots of bank account balances from dozens of financial institutions, as well as chat logs with other hackers and pictures of homegrown weed.
Some of the photos in that Imageshack account also appear on Kirtsov’s Vkontakte page, including images of vehicles he owns, as well as pictures of potted marijuana plants. Kirtsov’s Vkontakte profile says that in 2012 he was a faculty member of the Ozersk Technological Institute National Research Nuclear University.
The Vkontakte page lists Kirtsov’s occupation as a website called ozersk[.]today, which on the surface appears to be a blog about life in Ozersk. However, in 2019 the security firm Recorded Future published a blog post which found this domain was being used to host a malicious Cobalt Strike server.
Cobalt Strike is a commercial network penetration testing and reconnaissance tool that is sold only to vetted partners. But stolen or ill-gotten Cobalt Strike licenses are frequently abused by cybercriminal gangs to help lay the groundwork for the installation of ransomware on a victim network.
In August 2023, x999xx posted a message on Exploit saying he was interested in buying a licensed version of Cobalt Strike. A month earlier, x999xx filed a complaint on Exploit against another forum member named Cobaltforce, an apparent onetime partner whose sudden and prolonged disappearance from the community left x999xx and others in the lurch. Cobaltforce recruited people experienced in using Cobalt Strike for ransomware operations, and offered to monetize access to hacked networks for a share of the profits.
DomainTools.com finds ozersk[.]today was registered to the email address dashin2008@yahoo.com, which also was used to register roughly two dozen other domains, including x999xx[.]biz. Virtually all of those domains were registered to Maxim Kirtsov from Ozersk. Below is a mind map used to track the identities mentioned in this story.
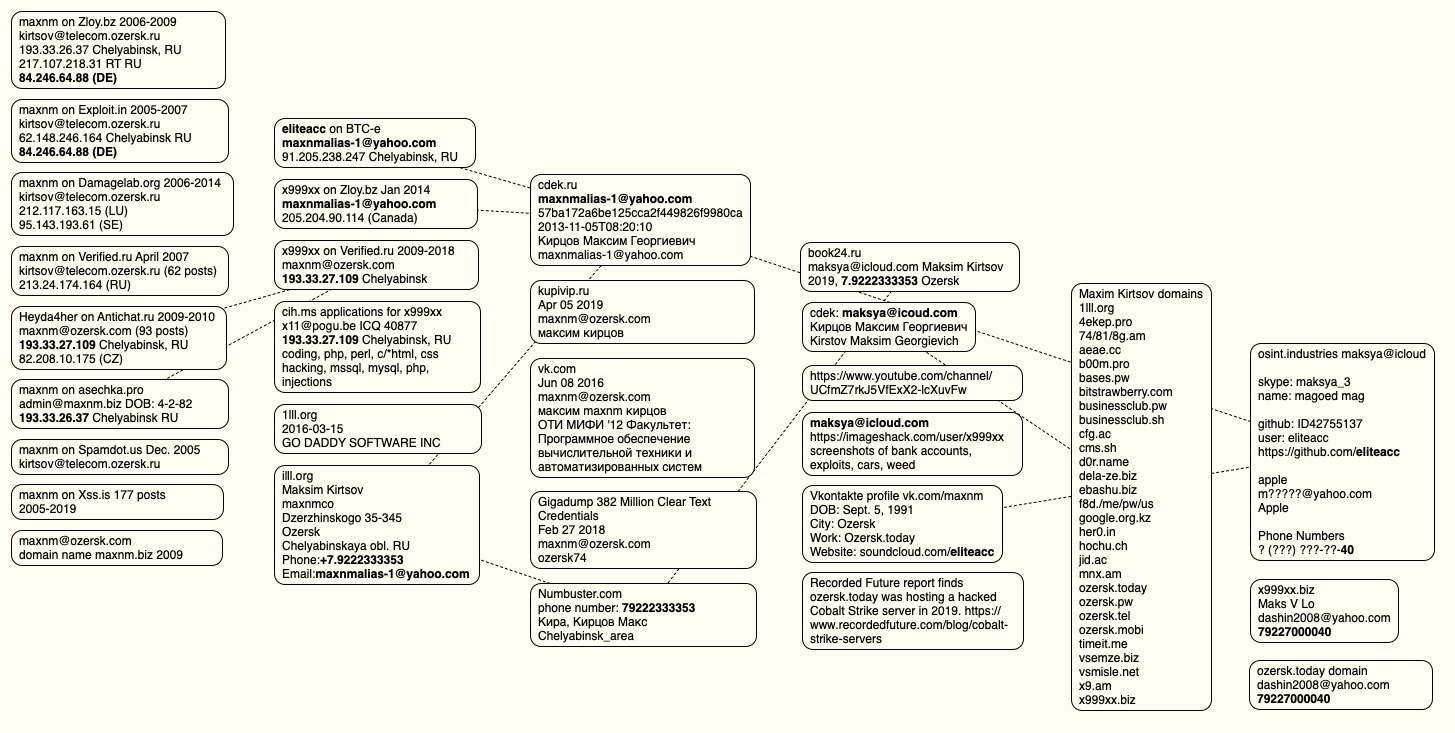
A visual depiction of the data points connecting x999xx to Max Kirtsov.
x999xx is a prolific member of the Russian webmaster forum “Gofuckbiz,” with more than 2,000 posts over nearly a decade, according to Intel 471. In one post from 2016, x999xx asked whether anyone knew where he could buy a heat lamp that simulates sunlight, explaining that one his pet rabbits had recently perished for lack of adequate light and heat. Mr. Kirtsov’s Vkontakte page includes several pictures of caged rabbits from 2015 and earlier.
CONFIRMATIONReached via email, Mr. Kirtsov acknowledged that he is x999xx. Kirtsov said he and his team are also regular readers of KrebsOnSecurity.
“We’re glad to hear and read you,” Kirtsov replied.
Asked whether he was concerned about the legal and moral implications of his work, Kirtsov downplayed his role in ransomware intrusions, saying he was more focused on harvesting data.
“I consider myself as committed to ethical practices as you are,” Kirtsov wrote. “I have also embarked on research and am currently mentoring students. You may have noticed my activities on a forum, which I assume you know of through information gathered from public sources, possibly using the new tool you reviewed.”
“Regarding my posts about selling access, I must honestly admit, upon reviewing my own actions, I recall such mentions but believe they were never actualized,” he continued. “Many use the forum for self-serving purposes, which explains why listings of targets for sale have dwindled — they simply ceased being viable.”
Kirtsov asserted that he is not interested in harming healthcare institutions, just in stealing their data.
“As for health-related matters, I was once acquainted with affluent webmasters who would pay up to $50 for every 1000 health-themed emails,” Kirtsov said. “Therefore, I had no interest in the more sensitive data from medical institutions like X-rays, insurance numbers, or even names; I focused solely on emails. I am proficient in SQL, hence my ease with handling data like IDs and emails. And i never doing spam or something like this.”
On the Russian crime forums, x999xx said he never targets anything or anyone in Russia, and that he has little to fear from domestic law enforcement agencies provided he remains focused on foreign adversaries.
x999xx’s lackadaisical approach to personal security mirrors that of Wazawaka, another top Russian access broker who sold access to countless organizations and even operated his own ransomware affiliate programs.
“Don’t shit where you live, travel local, and don’t go abroad,” Wazawaka said of his own personal mantra. “Mother Russia will help you. Love your country, and you will always get away with everything.”
In January 2022, KrebsOnSecurity followed clues left behind by Wazawaka to identify him as 32-year-old Mikhail Matveev from Khakassia, Russia. In May 2023, the U.S. Department of Justice indicted Matveev as a key figure in several ransomware groups that collectively extorted hundreds of millions of dollars from victim organizations. The U.S. State Department is offering a $10 million reward for information leading to the capture and/or prosecution of Matveev.
Perhaps in recognition that many top ransomware criminals are largely untouchable so long as they remain in Russia, western law enforcement agencies have begun focusing more on getting inside the heads of those individuals. These so-called “psyops” are aimed at infiltrating ransomware-as-a-service operations, disrupting major cybercrime services, and decreasing trust within cybercriminal communities.
When authorities in the U.S. and U.K. announced in February 2024 that they’d infiltrated and seized the infrastructure used by the infamous LockBit ransomware gang, they borrowed the existing design of LockBit’s victim shaming website to link instead to press releases about the takedown, and included a countdown timer that was eventually replaced with the personal details of LockBit’s alleged leader.
In May 2024, law enforcement agencies in the United States and Europe announced Operation Endgame, a coordinated action against some of the most popular cybercrime platforms for delivering ransomware and data-stealing malware. The Operation Endgame website also included a countdown timer, which served to tease the release of several animated videos that mimic the same sort of flashy, short advertisements that established cybercriminals often produce to promote their services online.
AWS approach to RAG evaluation could help enterprises reduce AI spending
AWS’ new theory on designing an automated RAG evaluation mechanism could not only ease the development of generative AI-based applications but also help enterprises reduce spending on compute infrastructure.
RAG or retrieval augmented generation is one of several techniques used to address hallucinations, which are arbitrary or nonsensical responses generated by large language models (LLMs) when they grow in complexity.
Intro to multithreaded JavaScript
The JavaScript language is one of the wonders of the software world. It is incredibly powerful, flexible, and versatile. One limitation of its fundamental design, however, is its single-threaded nature. Traditional JavaScript appears to handle parallel tasks, but that is a trick of syntax. To achieve true parallelism, you need to use modern multithreading approaches like web workers and worker threads.
Parallelism vs. concurrencyThe most basic way to understand the difference between parallelism and concurrency is that concurrency is semantic whereas parallelism is implementation. What I mean is that concurrency lets you tell the system (semantics) to do more than one thing at once. Parallelism simply performs multiple tasks simultaneously (implementation). All parallel processing is concurrent, but not all concurrent programming is parallel.
How to get started with GraphQL
Developed by Facebook and released as an open standard for all to use, GraphQL is intended as an alternative to REST APIs. Like REST, GraphQL provides a way to create and consume web-based APIs, but queries and returned data use formal schemas and a type system to guarantee consistency.
In this article, we’ll walk through the basics of designing and implementing a GraphQL API and discuss many of the key considerations and decisions you’ll make during the process.
GraphQL languages and frameworksIf you’re planning to use GraphQL as your web application API, there is a very good chance the language and data components you’re already using will support your efforts. GraphQL libraries are available for almost every major language in production use. Clients are available for C#/.NET, Go, Java and Android, JavaScript, Swift/Objective-C, and Python, and the server libraries cover even more ground.
SN 981: The End of Entrust Trust - Open SSH Vulnerability, SyncThing, Endtrust
- The regreSSHion Bug
- 50BTC moved
- Voyager 1 Update
- Email @ GRC
- SyncThing
- DNS queries
- Recall
- The End of Entrust Trust
Show Notes - https://www.grc.com/sn/SN-981-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to this show at https://twit.tv/shows/security-now.
Get episodes ad-free with Club TWiT at https://twit.tv/clubtwit
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Sponsors:
Rust types team moves forward on next-gen trait solver
The Rust types team has made significant progress on the next-generation trait solver, according to a June 26 blog post.
Work done to stabilize the use of the next-generation trait solver in coherence checking surfaced small behavior regressions and hangs, which caused delays. But the team is close to compiling the standard library and the compiler with the new solver enabled everywhere. They expect a long tail of minor issues and behavioral differences from the existing implementation. There also are open design questions that will need to be resolved prior to stabilizing the new implementation. The goal is to use the next-generation trait solver everywhere by default.
How to describe Java code with annotations
There are times when you need to associate metadata, or data that describes data, with classes, methods, or other elements in your Java code. For example, your team might need to identify unfinished classes in a large application. For each unfinished class, the metadata would include the name of the developer responsible for finishing the class and the class’s expected completion date.
Before Java 5, comments were Java's only flexible mechanism for associating metadata with application elements. But because the compiler ignores them, comments are not available at runtime. And even if they were available, you would have to parse the text to obtain crucial data items. Without standardizing how the data items were specified, they might be impossible to parse.
Qdrant unveils vector-based hybrid search for RAG
Open-source vector database provider Qdrant has launched BM42, a vector-based hybrid search algorithm intended to provide more accurate and efficient retrieval for retrieval-augmented generation (RAG) applications. BM42 combines the best of traditional text-based search and vector-based search to lower the costs for RAG and AI applications, Qdrant said.
Qdrant’s BM42 was announced July 2. Traditional keyword search engines, using algorithms such as BM25, have been around for more than 50 years and are not optimized for the precise retrieval needed in modern applications, according to Qdrant. As a result they struggle with specific RAG demands, particularly with short segments requiring further context to inform successful search and retrieval. Moving away from a keyword-based search to a fully vectorized based offers a new industry standard, Qdrant said.
Anthropic launches fund to measure capabilities of AI models
AI research is hurtling forward, but our ability to assess its capabilities and potential risks appears to be lagging behind. To bridge this critical gap, and recognize the current limitations in third-party evaluation ecosystems, Anthropic has started an initiative to invest in the development of robust, safety-relevant benchmarks to assess advanced AI capabilities and risks.
“A robust, third-party evaluation ecosystem is essential for assessing AI capabilities and risks, but the current evaluations landscape is limited,” Anthropic said in a blog post. “Developing high-quality, safety-relevant evaluations remains challenging, and the demand is outpacing the supply. To address this, today we're introducing a new initiative to fund evaluations developed by third-party organizations that can effectively measure advanced capabilities in AI models.”
Serverless cloud technology fades away
It is becoming increasingly evident that serverless technology is losing relevance and will soon fade away in the cloud technology space. Why did this happen? What can we learn from this evolution of technology?
When serverless computing first hit the streets over a decade ago as a cloud computing paradigm, it saved us from needing to handle detailed compute and storage configurations. Everything was done automatically at the time of execution. This seemed more evolution than revolution because PaaS systems were already doing an aspect of this type of computing.
How evolving AI regulations impact cybersecurity
While their business and tech colleagues are busy experimenting and developing new applications, cybersecurity leaders are looking for ways to anticipate and counter new, AI-driven threats.
It’s always been clear that AI impacts cybersecurity, but it’s a two-way street. Where AI is increasingly being used to predict and mitigate attacks, these applications are themselves vulnerable. The same automation, scale, and speed everyone’s excited about are also available to cybercriminals and threat actors. Although far from mainstream yet, malicious use of AI has been growing. From generative adversarial networks to massive botnets and automated DDoS attacks, the potential is there for a new breed of cyberattack that can adapt and learn to evade detection and mitigation.
Eclipse Theia IDE arrives for desktop, browser
The Eclipse Foundation has announced the release of the Eclipse Theia IDE. Based on the Theia cloud and desktop IDE framework implemented in TypeScript, the Theia IDE is avialable for Windows, Linux, and macOS and can be tried online.
With development led by EclipseSource CEO Jonas Helming, the Theia IDE was announced on June 27. The Theia IDE serves as an addition to the Eclipse Cloud DevTools ecosystem and provides an extensible coding experience across both desktop and browser environments. Developers can customize and control coding environments, offering greater productivity and creativity, the Eclipse Foundation said.